Press release
More and more women use espionage software to expose an infidelity
In many relationships, everyday life creeps in after a few years. The passion decreases and many couples feel the act of love over time as boring. Most do not want to end their relationship, but they secretly want an adventure with a foreign partner. The Internet offers in such a situation more and more opportunities for a fling. Often, many people start flirting through online portals such as Facebook or on dating sites.Women intuitively sense whether something is wrong in the relationship:
Men are hardly different from women. However, more and more women manage to expose the infidelity of their men. The reason is that women have a better "nose" for when something in their relationship changes to the negative. In such a situation, more and more women are looking for ways to gain clues about possible misconduct of the partner.
Surveillance programs can expose an infidelity:
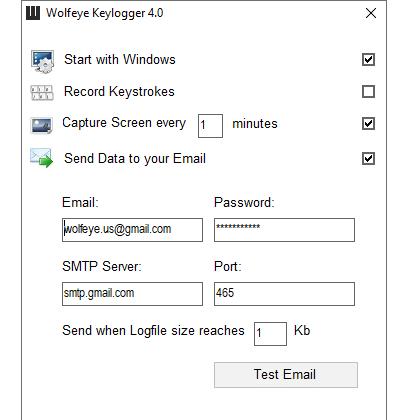
"Although men are often much more knowledgeable about technology than women, more and more women use surveillance programs to prove the infidelities," says Angel Gonzalez from https://www.wolfeye.us/ . The company has developed the Wolfeye Keylogger monitoring software, which has become increasingly popular with women, as the program is very easy to use and offers very good and stable monitoring functionalities.
This is amazing: many women do not even know what the term "keylogger" means. Nevertheless, more and more women are using such monitoring tools. On the Internet, it is becoming increasingly easier to obtain information about how to monitor a computer, what programs are needed, and how to use them. Many men, on the other hand, often know the term "keylogger" and know for what purposes such programs can be used. Many even have experience with the software and are familiar with the basic functions.
Keyloggers are programs that secretly record all keystrokes in the background. In this way, passwords to email and Facebook can be logged in the background. The visited websites are also saved. Wolfeye Keylogger even takes screenshots - screen captures - at regular intervals. All data can be sent to the supervisor by email. This allows the PC to be monitored remotely.
Monitoring the partner is illegal:
The program should not actually be used to monitor the partner: Wolfeye Keylogger is a keylogger that can theoretically be used for illegal purposes. This is of course not allowed: Wolfeye may only be installed and executed on your own computer. The employment on strange computers without consent of the owner is forbidden!
The software is legal but actually intended to monitor children's Internet behavior, for example. The keylogger should inform the user at an early stage if the child is bullied on the Internet or consumes inappropriate content. Anyone who is afraid that others gain unauthorized access to their own computer, such software can also install on their own PC and will be informed of such access.
Employees in companies may only be supervised with the consent of:
While the proportion of women who use spy programs illegally use them to monitor the partner, the purpose of most of the men using such programs is different: they use surveillance more often to monitor employees in their own companies. However, this mission is also critical and not always legal: Employers may use such software to monitor their employees only if they have previously been informed in writing.
Especially medium-sized companies, such as architectural firms, often have to worry about their employees working on their own private projects during their working hours and earning something on the side. For this reason, the use in companies is also often used.
Conclusion:
Because the use of a keylogger to expose an infidelity is illegal, many users have problems when it comes to confronting the stranger that they know about the infidelity. How should one explain to the partner how it has been known? The same problem can also arise in employee monitoring companies.
wolfeye.us specializes in developing security software solutions for business and residential customers.
Angel Gonzalez
Security Software Solutions
Hoellbergstr. 4A
60431 Frankfurt am Main
mail@windows-keylogger.com
Phone +49 151 23 27 88 66
This release was published on openPR.
Permanent link to this press release:
Copy
Please set a link in the press area of your homepage to this press release on openPR. openPR disclaims liability for any content contained in this release.
You can edit or delete your press release More and more women use espionage software to expose an infidelity here
News-ID: 1756912 • Views: …
More Releases from Security Software Solutions

How employees are monitored in the home office
Surfing the Internet, Turning Off the Screen - Is That Work? In the corona crisis, spy software is booming, with which bosses have everything under control.
A few weeks ago, bank employees received an email from the boss. It said: You are under observation! We evaluate your keystrokes! We save your visited websites! And every 5 minutes we take a screenshot of your screen! We can also see your computer's live…
8 Situations in which you should use a keylogger software
Keylogger softwares are becoming more popular. This is because people and businesses are getting smarter. They're learning that its better to be prepared. Keyloggers can be helpful for businesses and personal computers in the event of many situations. But first, lets talk about what keyloggers are.
What are keyloggers?
Keyloggers are also refered to as PC monitoring software. A keylogger is a software that records everything that is typed into a computer.…
More Releases for Internet
Quantum Internet Alliance launches Quantum Internet Application Challenge
Quantum enthusiasts get a chance to co-create the future quantum internet
DELFT, THE NETHERLANDS-The Quantum Internet Alliance (QIA) has announced the launch of its first ever Quantum Internet Application Challenge (https://quantuminternetalliance.org/quantum-internet-application-challenge-2023/), an initiative encouraging quantum enthusiasts to take part in shaping the future of the quantum internet.
"The role of the community-from students and enthusiasts to scientists and industry leaders-in our mission of building a global quantum internet is pivotal. And the…
Rural Internet Market is Booming Worldwide | AT&T Internet, Ziply Fiber, HughesN …
The latest study released on the Global Rural Internet Market by AMA Research evaluates market size, trend, and forecast to 2028. The Rural Internet market study covers significant research data and proofs to be a handy resource document for managers, analysts, industry experts and other key people to have ready-to-access and self-analyzed study to help understand market trends, growth drivers, opportunities and upcoming challenges and about the competitors.
Download Sample Report…
Internet of Things Devices Market - Extending Internet Connectivity Beyond Stand …
This study researches the market size of Internet of Things Devices in United States, European Union and China, presents the Internet of Things Devices production, consumption, value, product price, market share and growth rate by companies, type and application, history breakdown data from 2013 to 2018, and forecast to 2025.
For top companies in United States, European Union and China, this report investigates and analyzes the production, value, price, market share…
Internet of Things Market - ZigBee Leads Global Internet of Things Market
Global Internet of Things Market: Overview
The Internet of Things refers to the interrelated devices that are able to transfer data over a network without requiring computer and human interaction devices. Internet of Things is directly and indirectly associated with daily lifestyle products across the globe. Internet connectivity is one of the major requirements of different application as it is expected to grow at high rate in next forecast period. Furthermore,…
Sextillion Internet Possibilities
arvato Systems is introducing a new Internet Protocol Standard, IPv6
arvato Systems (Gütersloh, Germany) -- The number of IP addresses available is in decline. Without them, the internet cannot function. That’s why arvato Systems is heeding the Internet Society’s call to action, and participating in this year’s IPv6 launch day. The new protocol will exponentially expand the number of available IP addresses.
IPv6, or ‘Internet Protocol Version 6’ is a new Internet…
New Internet Marketing Platform Released to Help Internet Marketers
The Six Figure Mentors, a new UK-based company, is finally ready to be launched in cyberspace on December 9th, 2010.
Created by Stuart Ross and Daniel Wagner, two very experienced Internet marketers, the new platform aims at teaching new Internet marketers how to set and manage their own business. According to Ross, "I created this system to address the frustrations I had, which are shared by the majority of internet…
