Press release
8 Situations in which you should use a keylogger software
Keylogger softwares are becoming more popular. This is because people and businesses are getting smarter. They're learning that its better to be prepared. Keyloggers can be helpful for businesses and personal computers in the event of many situations. But first, lets talk about what keyloggers are.What are keyloggers?
Keyloggers are also refered to as PC monitoring software. A keylogger is a software that records everything that is typed into a computer. The purchaser of the keylogger software can then retrieve and review that record.
The features of each keylogger software will vary based on the brand name. But some keylogger software will also take screenshots of the computer. You may even be able to automate them and regulate how often they are taken.
The PC users wont know that they're computer usage is being recorded. Now you may be wondering when would you use a keylogger?
8 situations in which you should use a keylogger.
1). Your computer crashes
If you've used a computer more than a few times in your lifetime, then you've probably had one crash on you. This can be a very bad situation if you were in the middle of typing something important.
If your computer crashes unexpectedly its very likely every thing you were typing was deleted from your computer for good.
You can be prepared for this situation by having a keylogger. A keylogger will have recorded every stroke typed, so it will have all your typed data backed up and retrievable.
A keylogger can prevent a lot of problems and fustration in your business and personal life.
2). You suspect your computer may have been tampered with or accessed without your permission.
If you are suspicious that your computer may have been tampered with or someone was searching through your personal files, a keylogger can help.
A keylogger will be able to tell you what was typed into your computer. Keylogger software will also show you any files, websites or apps that were opened on your PC.
A keylogger is a really good idea if you have personal information or data on your computer.
3). You have a child that uses a computer
The internet can be a great tool for children. Whether it's for learning or having fun. But it can also be dangerous.
Young children should be monitored when using the internet. They may venture onto sites that are inappropriate for their age or they may some how talk to strangers online.
You may also want to monitor your teenagers PC if you suspect they are being cyberbullied or getting into trouble. There are other situations where monitoring your teenagers PC could also be appropriate.
Keyloggers will show passwords to accounts and emails. This will be very useful if you need to access your teens social media for any reason.
You may just want to monitor your children's overall internet surfing habits. Lots of parents monitor and restrict the amount of time their children spend in front of a computer screen.
Keyloggers can help parents protect their children online.
4). You suspect your significant other is cheating on you.
Using a keylogger for this reason may be seen as unethical by some. However, a keylogger can still be very useful in this situation.
You can use a keylogger to track every keystroke, and gain access to a variety of information that will help clear your suspicions.
You can access messages and chats to see who they've been talking to from the PC. You can also accesses screenshots for a better view.
Be sure to only use a keylogger if you own the PC.
5). You have employees who work on your computers
Businesses often have employees who do most of their work from company owned computers. When you have others using computers that you own, its always important to monitor it.
This is because employees will visit unauthorized websites, either intentionally or unintentionally. This may result in viruses or hackers accessing company files.
Employees may also participate in illegal or inappropriate activities from your computer.
A keylogger can be a helpful tool in monitoring your business PCs.
6). You want to improve the productivity of your employees
By monitoring the keystrokes you can also see how productive your employees are. You may find that you have very productive employees or very unproductive employees.
You can decide to explore each employees habits or review the computer usage as a company.
Either way the results of a keylogger can you decide what steps to take next for your business.
A keylogger may save you alot of money as you weed out employees who spend most of company time on social media.
Getting a picture of your company's productivity can be vital to your success.
7). In the event that your PC is stolen
If your PC is stolen, a keylogger can you help you find who stole it and get it back.
Although a keylogger isnt going to give you a gps location of your PC, you can view everything happening on it. This means you can easily find evidence to help identify who has your PC.
Monitoring the thief's internet usage can be a big clue to who they are. Any activities performed on your laptop can be monitored by you.
Whether they are accessing their email, or chatting with a friend on Facebook, its all evidence. Once you've gathered enough evidence you can work with your local police station to retrieve your device.
A PC monitoring software can become your best friend if your PC is stolen.
8). You want to monitor yourself
Monitoring your own keystrokes can be the first step to becoming a better you. A keylogger will show you all the activities that you've done on your PC.
Your keylog record can be a fact based method to monitor your habits. You can view how often you visit certain sites, and how productive you've been.
Overtime a keylogger could have benefits to your personal life and time management. Review your keylog record and learn from it.
Reevaluate how you spend your time, have you been googling pointless things when your supposed to working? Have you been visiting that one website that sells all your favorite brands way too often?
Your keylogger will provide proof of your habits, forcing you to confront them.
Using a keylogger may improve aspects of your personal life.
Keyloggers arent only used in these situations. But these are common situations in which you could use the power of a keylogger.
Keyloggers are great for recovering from and preventing problems. It's important that you get a keylogger before the problem occurs.
Buying a keylogger
There are many versions of PC monitoring software available. But they arent all made equal.
You should first identify what kind of operating systems the keylogger software is compatible with. Then you should verify that your PC has a compatible operating system.
Skipping this step can cause you to lose, time and money on a keylogger software that you cant use.
Before deciding on a keylogger you should also always review its features, so you know what it has to offer.
One of the best PC monitoring softwares for Windows currently on the market is the Wolfeye Keylogger ( www.wolfeye.us ).
There are plenty of reasons to love the Wolfeye Keylogger.
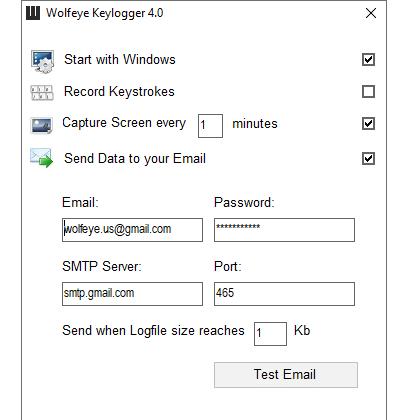
Wolfeye Keylogger
The Wolfeye Keyblogger is a computer monitoring software for Windows.
It supports
- Windows 10
- Windows 8
- Windows 7
- Windows Vista
- Windows XP
Features:
- Keystrokes
The Wolfeye Keylogger tracks every single keystroke including passwords. You can also see chats and instant messages
- Screenshots
The Wolfeye Keylogger allows you to have screenshots taken of your PC so you can see the screen exactly as the PC user does. You can automate screenshots to be taken as often as 1 every minute.
- Remote Retrieval
You can retrieve your record of keystrokes and screenshots from anywhere you can access the internet. The Wolfeye Keylogger gives you the option to have retieve your records by email.
If you prefer you also have the option of storing your records in a log file.
The Wolfeye Keylogger software is also a great value. Upon purchasing you'll receive 5 PC licenses, all for one price.
Whether you're protecting your family or your business you cant go wrong with a Wolfeye Keylogger.
Using a keylogger
Once you've purchased a keylogger software you must learn to install it. Instructions for how to install your keylogger will vary based on the specific keylogger.
But its generally pretty easy.
How to install
Here's how most keyloggers are installed.
1). If you use antivirus programs you will need to adjust the settings to allow the program to download.
2). Simply download the software.
3) Complete the installation of the software.
4). Adjust settings as necessary
There are many situations where a keylogger would come in handy. Its a great way to be prepared for internet usage problems in the home and in business settings.
You should always use all keylogger software responsibly. Never use it to harm or steal from others.
Angel Gonzalez
Security Software Solutions
Höllbergstr. 4A
60431 Frankfurt am Main
www.wolfeye.us
We specialize in digital surveillance technology with a focus on monitoring software. Since 2011, we have been implementing customized software solutions for securing sensitive data for companies, banks, government institutions, schools, public authorities and discerning private customers. Our products are successfully used in over 80 countries.
This release was published on openPR.
Permanent link to this press release:
Copy
Please set a link in the press area of your homepage to this press release on openPR. openPR disclaims liability for any content contained in this release.
You can edit or delete your press release 8 Situations in which you should use a keylogger software here
News-ID: 1876277 • Views: …
More Releases from Security Software Solutions

How employees are monitored in the home office
Surfing the Internet, Turning Off the Screen - Is That Work? In the corona crisis, spy software is booming, with which bosses have everything under control.
A few weeks ago, bank employees received an email from the boss. It said: You are under observation! We evaluate your keystrokes! We save your visited websites! And every 5 minutes we take a screenshot of your screen! We can also see your computer's live…

More and more women use espionage software to expose an infidelity
In many relationships, everyday life creeps in after a few years. The passion decreases and many couples feel the act of love over time as boring. Most do not want to end their relationship, but they secretly want an adventure with a foreign partner. The Internet offers in such a situation more and more opportunities for a fling. Often, many people start flirting through online portals such as Facebook or…
More Releases for Keylogger
Password Hacking Software Market Hits New High | Major Giants Medusa, Wfuzz, Ett …
HTF MI just released the Global Password Hacking Software Market Study, a comprehensive analysis of the market that spans more than 143+ pages and describes the product and industry scope as well as the market prognosis and status for 2025-2033. The marketization process is being accelerated by the market study's segmentation by important regions. The market is currently expanding its reach.
Major Manufacturers are covered: John the Ripper, Hashcat, Hydra, Cain…
Spyrix Unveils Enhanced Employee Monitoring Software for 2024 to Boost Workforce …
Spyrix, one of the leading companies in software development, is proud to notify all about the release of employee monitoring software update in 2024. It is designed to help businesses enhance employees' productivity at the workplace and security of the company's data through preventing confidential data leakage.
Post-pandemic times maintain the tendency for remote and hybrid work modes. As a result, it is still challenging to monitor the activities of such…
How employees are monitored in the home office
Surfing the Internet, Turning Off the Screen - Is That Work? In the corona crisis, spy software is booming, with which bosses have everything under control.
A few weeks ago, bank employees received an email from the boss. It said: You are under observation! We evaluate your keystrokes! We save your visited websites! And every 5 minutes we take a screenshot of your screen! We can also see your computer's live…
More and more women use espionage software to expose an infidelity
In many relationships, everyday life creeps in after a few years. The passion decreases and many couples feel the act of love over time as boring. Most do not want to end their relationship, but they secretly want an adventure with a foreign partner. The Internet offers in such a situation more and more opportunities for a fling. Often, many people start flirting through online portals such as Facebook or…
Specialized Threat Analysis and Protection (STAP) Market Size, Share, Key Player …
The intense need to improve the quality of protection, and increased network complexity of specialized threat protection and analysis, are the major growth drivers of the specialized threat analysis and protection market. Growth in the number of enterprise security requirements has increased the demand for software as a service (SaaS) based specialized threat analysis, and protection solutions which has beaten the demand for traditional IT security solutions.
Request for a free…
Exceptional notice of dismissal for working hours fraud
Fraud relating to one’s working hours may constitute good cause justifying exceptional notice of dismissal. Having said that, a ruling of the Landesarbeitsgericht (LAG) Hamm [Regional Labour Court of Hamm] shows that for this to happen there needs to be admissible evidence to this end.
GRP Rainer Lawyers and Tax Advisors in Cologne, Berlin, Bonn, Düsseldorf, Frankfurt, Hamburg, Munich, Stuttgart and London conclude: An employment contract can be terminated with exceptional…