Press release
How to Protect Yourself Online: Internet Safety for Beginners
The internet is now a core pillar of our daily lives, both personally and professionally. We work, socialize, and even shop on the Internet.But in doing so, it's somewhat inevitable that we put our data and privacy at risk.
Things like our personal information, account credentials, and even financial data-we have to put them out into the internet, at risk of getting breached and stolen by hackers, fraudsters, and other cyber criminals.
In fact, according to the Identity Theft Resource Center, there have been over 1 billion data breach victims in 2024 so far. That's 1 out of every 8 people in the world.
In this article, we'll go through the basics of cybersecurity, from the common forms of cyberattacks to basic practices that everyone should be implementing in their internet use.
4 Common Forms of Cyberattacks
Cyberattacks can take form in many ways. Here are some of the most common threats that every internet user should be aware of.
1. Phishing Attacks
Phishing attacks refer to fake emails or websites that are designed to trick you into revealing personal information like passwords or credit card numbers. These emails and websites often tell you that you've won prize money or that there is a legal complaint against you and that you must click a certain link to proceed. Clicking that link is dangerous and could put your data into that email's sender.
2. Malware
Malware refers to malicious software that can damage your devices, steal data, or grant unauthorized access to hackers. They're often hidden in the various files we download on the internet.
3. Identity Theft
We often input our personal information when creating accounts or shopping online. Doing so on suspicious websites can leave your information up for grabs, allowing identity thieves can use your personal information to commit fraud or other crimes.
4. Public Wi-Fi Risks
Using public Wi-Fi is risky because, technically speaking, the owner of the Wi-Fi network can monitor everything you do while on their connection.
How to Protect Yourself Online: Cybersecurity Measures
So, what should we do about these attacks?
Below, we've listed the ten most important internet practices that will minimize the risk of your online information and privacy from getting breached.
1. Create Strong Passwords
Weak passwords are arguably the most common entry points for cybercriminals.
A strong password should always include a combination of:
● Uppercase and lowercase letters;
● Numbers;
● Special characters.
Avoid using easily guessable information like your name, birth date, or sequential phrases like "123456" or "ABCDEFG." Additionally, avoid reusing passwords across different sites.
Creating and remembering complex passwords-and doing so every time you create a new account-can definitely be a hassle. But it's even more of a headache for your account to get breached.
2. Enable Two-Factor Authentication (2FA)
Two-factor authentication or 2FA refers to how you must verify your identity twice when you log in to your account or access data.
So, for example, when you log in to a website with your password, the website may also ask you to input a code sent to the phone number or email address you've associated with your account.
Many popular platforms, including social media websites like Google and Facebook, and even (and especially) banking apps, offer 2FA as an option. Enable it wherever possible to add a second line of defense against unauthorized access.
3. Use a Reliable Antivirus Program
Antivirus software is your first line of defense against malware. It detects and neutralizes harmful files and software before they can harm your device. Ensure that your antivirus program is not only constantly active but also updated regularly, as new types of malware are constantly emerging.
For Windows users, Windows Defender is plenty enough for most people.
4. Use a VPN
A Virtual Private Network (VPN) is a tool that encrypts your internet connection, making it difficult for hackers or third parties to intercept your data. It does so by masking your IP address, allowing you to browse the internet anonymously.
This is incredibly useful, especially when you're using public Wi-Fi.
Getting one is now incredibly easy, and there are even VPN download APK options ( https://surfshark.com/download/android ) for those who don't want to use app stores.
5. Be Wary of Phishing Schemes
As discussed above, falling for a phishing scheme is arguably the most common way people get their data stolen. To avoid falling victim:
● Verify the Sender
Many phishing emails will claim to be from legitimate organizations (such as large businesses or government agencies). Always check the sender's email address and ensure that it's actually that organization's email.
● Avoid Clicking Suspicious Links
Always hover over links to see where they lead before clicking.
● Double-CheckUrgent Requests
Phishing emails tend to sound urgent in getting people to click these links immediately. They may claim that you've won money or that you're about to face legal consequences-and that you must act immediately on it.
If unsure about an email, try contacting the organization directly through other official channels.
6. Keep Your Software and Devices Updated
Always update your devices and software, as these typically include patches for security vulnerabilities.
After all, hackers frequently exploit outdated software to gain access to these devices and systems. If possible, set your devices and software programs to install updates automatically.
7. Limit the Personal Information You Share
Minimize the amount of personal information you share on public platforms like social media websites. Ask yourself: do you really need to include your address, phone number, and other personal information on your social media account?
After all, at any moment, your account can get hacked, or these platforms can also get compromised, such as when Yahoo! had 3 billion accounts breached.
8. Practice Safe Downloading
Only download software and files from trusted sources. Cybercriminals often disguise malware as legitimate downloads, especially with pirated content.
To stay safe:
● Verify the file source
Only download from legitimate websites or the official app stores.
● Avoid unsolicited download links in emails or ads.
These are likely phishing schemes or malware attacks.
● Double-check your download's file type
Know what file type you should be downloading.
Images are often PNG, JPG, or WEBP.
Documents are often in PDF.
Audio files are often in MP3 and video files in MP4, MKV, or AVI.
Unless you're downloading a video game, EXE files are massive red flags. Do not run these EXE files, as they will most likely install malware into your device.
9. Monitor Your Accounts for Unusual Activity
It's always good to be vigilant. Even if you've never experienced a cyberattack before, make sure to regularly review your bank statements, credit card transactions, and online accounts for suspicious activity.
The earlier you detect them, the earlier you can report such activities to your bank or service provider and safeguard your account.
Many services also offer alerts for unusual account activity (such as log-ins from other geographic locations). Enable these notifications to stay informed.
10. Educate Yourself and Others
Just as technology is constantly evolving, so too are cybersecurity threats. It's a good idea to keep yourself up to date about the latest cybersecurity threats and best practices.
Also, share your knowledge with friends, family, and colleagues to create a network of digitally aware individuals. This is particularly true if you share accounts with family members (although this is also somewhat unadvisable) who may not be the most digitally literate, such as children or elderly members.
Conclusion
Internet safety is getting increasingly more important in a world that's also becoming more and more digital-but it doesn't need to be complicated or intimidating.
Simply being aware and regularly implementing these cybersecurity measures will ensure that you can use the internet safely and privately.
Marica 25 G Plovdiv, Bulgaria
- ESBO Ltd is a leading company for innovative digital marketing services with a focus on several countries around the world.
This release was published on openPR.
Permanent link to this press release:
Copy
Please set a link in the press area of your homepage to this press release on openPR. openPR disclaims liability for any content contained in this release.
You can edit or delete your press release How to Protect Yourself Online: Internet Safety for Beginners here
News-ID: 3905613 • Views: …
More Releases from ESBO ltd

Supporting Compliance with Law Firm Consultants
In the U.S., law firm non-compliance costs an average $14.82 million per year, nearly triple the cost of compliance. This can be attributed to the ever-expanding regulatory expectations and the evolution of professional standards. However, it's the responsibility of every law firm to treat compliance as a key part of how the organization operates, and not just as a background task.
As regulatory expectations expand across data protection, financial transparency,…

How to plan moving with kids
How to plan moving with kids
Moving is always a big event for a family, but when children are part of the picture, it can feel like you're juggling ten things at once. Between packing boxes, sorting paperwork, and saying goodbye to a familiar home, kids often pick up on the stress just as much as adults do. Some families choose to bring in professional help, like movers in Airdrie https://easymovingcalgary.com/airdrie-movers/…

How to Read Market Cycles Like a Professional Trader
Market cycles represent the natural rhythm of financial markets as they move through periods of growth, peak performance, decline, and recovery. These cycles occur across all timeframes, from short-term daily fluctuations to multi-year trends that shape entire economic eras. When you learn to identify these patterns, you gain a significant advantage in timing your trades and investment decisions.
Professional traders don't rely on luck or gut feelings. They study these…
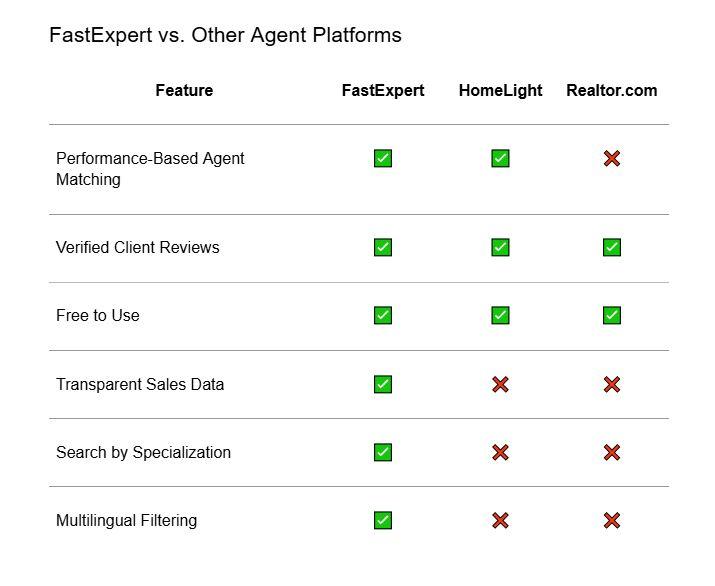
FastExpert Review: Is This Agent-Matching Platform Worth It?
When you're buying or selling a home, one of the most important decisions you'll make is choosing the right real estate agent. But with so many agents out there, how do you know which agents are experienced and right for what you need?
We've looked at countless online services that claim to help you find the best real estate agent. There are a lot out there, and they promise you the…
More Releases for Internet
Quantum Internet Alliance launches Quantum Internet Application Challenge
Quantum enthusiasts get a chance to co-create the future quantum internet
DELFT, THE NETHERLANDS-The Quantum Internet Alliance (QIA) has announced the launch of its first ever Quantum Internet Application Challenge (https://quantuminternetalliance.org/quantum-internet-application-challenge-2023/), an initiative encouraging quantum enthusiasts to take part in shaping the future of the quantum internet.
"The role of the community-from students and enthusiasts to scientists and industry leaders-in our mission of building a global quantum internet is pivotal. And the…
Rural Internet Market is Booming Worldwide | AT&T Internet, Ziply Fiber, HughesN …
The latest study released on the Global Rural Internet Market by AMA Research evaluates market size, trend, and forecast to 2028. The Rural Internet market study covers significant research data and proofs to be a handy resource document for managers, analysts, industry experts and other key people to have ready-to-access and self-analyzed study to help understand market trends, growth drivers, opportunities and upcoming challenges and about the competitors.
Download Sample Report…
Internet of Things Devices Market - Extending Internet Connectivity Beyond Stand …
This study researches the market size of Internet of Things Devices in United States, European Union and China, presents the Internet of Things Devices production, consumption, value, product price, market share and growth rate by companies, type and application, history breakdown data from 2013 to 2018, and forecast to 2025.
For top companies in United States, European Union and China, this report investigates and analyzes the production, value, price, market share…
Internet of Things Market - ZigBee Leads Global Internet of Things Market
Global Internet of Things Market: Overview
The Internet of Things refers to the interrelated devices that are able to transfer data over a network without requiring computer and human interaction devices. Internet of Things is directly and indirectly associated with daily lifestyle products across the globe. Internet connectivity is one of the major requirements of different application as it is expected to grow at high rate in next forecast period. Furthermore,…
Sextillion Internet Possibilities
arvato Systems is introducing a new Internet Protocol Standard, IPv6
arvato Systems (Gütersloh, Germany) -- The number of IP addresses available is in decline. Without them, the internet cannot function. That’s why arvato Systems is heeding the Internet Society’s call to action, and participating in this year’s IPv6 launch day. The new protocol will exponentially expand the number of available IP addresses.
IPv6, or ‘Internet Protocol Version 6’ is a new Internet…
New Internet Marketing Platform Released to Help Internet Marketers
The Six Figure Mentors, a new UK-based company, is finally ready to be launched in cyberspace on December 9th, 2010.
Created by Stuart Ross and Daniel Wagner, two very experienced Internet marketers, the new platform aims at teaching new Internet marketers how to set and manage their own business. According to Ross, "I created this system to address the frustrations I had, which are shared by the majority of internet…
