Press release
Research reveals: Over half a million payment cards stolen by malware
Over 600,000 payment cards compromised as malware as a service continues to thrive.As malware becomes an increasingly common tool for payment card theft, a recent research conducted by cybersecurity company NordVPN has revealed alarming information. Over 600,000 payment cards were compromised worldwide, with their details later sold on the dark web.
Adrianus Warmenhoven, a cybersecurity advisor at NordVPN, explains, "The malware didn't just steal the victims' payment card details. Most of the stolen payment cards' info came with a big bonus for cybercriminals - users' autofill information and account credentials. This additional information opens doors to an even wider range of attacks, including from identity theft, online blackmail, and cyber extortion."
The study showed that as many as 99% of the stolen cards included additional data, such as the victim's name, computer files, and saved credentials.
Malware as a service: A cybercriminal's payday
Cybercriminals use malware as a service, or subscription-based malware tools, for information theft. They function like your regular subscription - you pay a fee, and you get access to various data-stealing features.
"Malware is often used as a 'weapon of mass infection' because the results are reproducible at scale, even for relatively unskilled people. The payment card thieves are not 'cyber' criminals in the first place - they are criminals that have found a new tool to do what they would have done anyway," says Warmenhoven.
Malware as a service is available to buy for as little as $100-150 per month from specialized dark web marketplaces. The providers of malware go the extra mile to support their customers, often providing extensive guidance, user guides, and dedicated forums where newbies can get help.
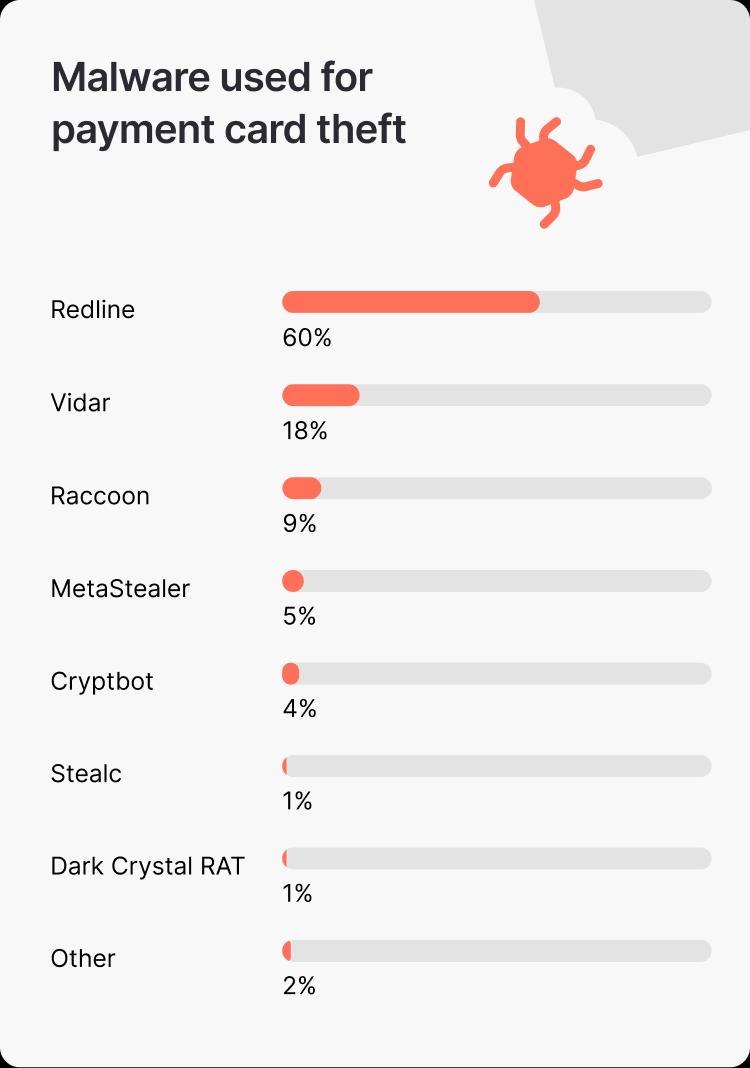
Spotlight on Redline - a cybercriminal's top choice
The research revealed that six out of 10 payment cards (60%) were stolen using sophisticated stealer, Redline.
Warmenhoven explains, "Redline is a significant threat due to its affordability, effectiveness, and accessibility. It's easily deployed through social engineering, continually adapts to evade detection, and is supported by dedicated Telegram channels, making it especially dangerous and accessible to novice cybercriminals."
Redline infiltrates devices via various methods that demand vigilance, such as phishing emails, exploiting software vulnerabilities, deceptive ads, and compromised public USB ports. Sophisticated techniques like man-in-the-middle and remote code attacks are also employed to deliver malware directly.
The unfortunate fact is that stolen data is sold and used incredibly quickly - often in a matter of hours. Cybercriminals know that the quicker they exploit the stolen payment card details, the higher the chance their fraudulent transactions will go through.
Visa cards and American users are the most targeted in widespread payment card theft
All payment cards are at risk of theft. However, payment cards from the most popular providers may be stolen more often because more people use them. The research showed that over half (54%) of the 600,000 cards were Visa, and a third (33%) were Mastercard cards.
Payment card theft is particularly rampant in the U.S., with most stolen payment card details coming from American users. However, payment card theft also severely impacts users in several other countries, such as Brazil, India, Mexico, and Argentina.
How to build a strong defense against malware
Adrianus Warmenhoven, a cybersecurity advisor at NordVPN, offers these essential tips to enhance online security and safeguard against malware:
Learn to spot phishing: Phishing emails and texts are often responsible for malware infections. Knowing the most common signs of phishing is crucial.
Use strong passwords: Creating long, complex, and unique passwords helps protect your accounts. For easy and secure password management, consider using NordPass.
Secure accounts with MFA: Setting up multi-factor authentication on your accounts adds an extra layer of security, which can prove incredibly useful if someone gets hold of your credentials.
Avoid shady downloads: Avoid downloading software, apps, or updates from unofficial sources - get them from app stores or official websites instead.
Use NordVPN's Threat Protection Pro: It blocks dangerous sites and scans files during download to prevent malware infections.
Use dark web monitoring tools: Dark Web Monitor continuously scans the dark web for your credentials and sends an alert if your email appears in a leaked database.
Agne Augustene
NordVPN | Public Relations
agne@nordsec.com
Švitrigailos g. 36, Vilnius, 03230 Vilniaus m. sav., Lithuania
NordVPN is the world's most advanced VPN service provider, chosen by millions of internet users worldwide. The service offers features such as dedicated IP, Double VPN, and Onion Over VPN servers, which help to boost your online privacy with zero tracking. One of NordVPN's key features is Threat Protection Pro, a tool that blocks malicious websites, trackers, and ads and scans downloads for malware. The latest creation of Nord Security, NordVPN's parent company, is Saily - a global eSIM service. NordVPN is known for being user friendly and can offer some of the best prices on the market. This VPN provider has over 6,400 servers covering 111 countries worldwide. For more information, visit https://nordvpn.com.
This release was published on openPR.
Permanent link to this press release:
Copy
Please set a link in the press area of your homepage to this press release on openPR. openPR disclaims liability for any content contained in this release.
You can edit or delete your press release Research reveals: Over half a million payment cards stolen by malware here
News-ID: 3598882 • Views: …
More Releases from NordVPN
The most prominent British women in the world of technology
Female IT influencers who are shaping technology
Even though the number of British women working in the technology sector increased to 31% last year, they only make up 10% of tech leadership, according to the Harvey Nash Tech Survey 2021. Given the fact that worldwide IT spending is projected to total $3.8 trillion in 2021, women are misrepresented where the potential to grow and advance in one's career is…
More Releases for VPN
Mobile VPN Market Growing with a Surprising Strength One Shouldn't Overlook | Th …
The Mobile VPN Market has witnessed continuous growth in the past few years and is projected to grow at a good pace during the forecast period of 2024-2032. The exploration provides a 360° view and insights, highlighting major outcomes of Mobile VPN industry. These insights help business decision-makers to formulate better business plans and make informed decisions to improve profitability. Additionally, the study helps venture or emerging players in understanding…
Mobile VPN Market Worth Observing Growth: Proton VPN, Speed VPN, SurfEasy VPN
HTF Market Intelligence added research publication document on Global Mobile VPN Market breaking major business segments and highlighting wider level geographies to get deep dive analysis on market data. The study is a perfect balance bridging both qualitative and quantitative information of Mobile VPN market. The study provides valuable market size data for historical (Volume** & Value) from 2014 to 2018 which is estimated and forecasted till 2026*. Some are…
Exclusive Report Virtual Private Network (VPN) Market 2019 Growing with Major Em …
Virtual Private Network (VPN) Market 2019 Industry Research Report study provides information on market trends and development, drivers, capacities, technologies, and on the changing dynamics of Virtual Private Network (VPN) Market. A thorough analysis of these elements has been accepted for defining the future growth prospects of the global Virtual Private Network (VPN) market.
Get Sample Copy of this Report -https://www.orianresearch.com/request-sample/1011752
Market Overview: The Global Virtual Private Network (VPN) market 2019 research…
Virtual Private Network (VPN) Market 2019 Global Analysis By Key Players – Pri …
MarketResearchNest.com presents “Global Virtual Private Network (VPN) Market Status and Future Forecast 2015-2024” new document to its studies database. The records spread across 150 with more than one tables and figures in it.
This comprehensive Virtual Private Network (VPN) Market research report includes a brief on these trends that can help the businesses operating in the industry to understand the market and strategize for their business expansion accordingly. The research report…
Virtual Private Network (VPN) Market Gaining Traction Worldwide by Major Vendors …
Virtual private networks are designed to expand a network securely from a private area, such as an enterprises or a home, through a public network, as if the network was directly connected. A large number of Internet users across the world rely on virtual private network (VPN) applications and software to access websites without the threat of spying or unsolicited monitoring of their online movements. VPN tools enable users to…
Firewall And Virtual Private Network (VPN) Market 2019 Precise Outlook - TorGuar …
Global Firewall And Virtual Private Network (VPN) Market Insights, Forecast To 2025
This report tracks the major market events including product launches, development trends, mergers & acquisitions and the innovative business strategies opted by key market players. Along with strategically analyzing the key markets, the report also focuses on industry-specific drivers, restraints, opportunities and challenges in the Firewall And Virtual Private Network (VPN) market. This research report offers in-depth analysis…