Press release
Cryptographic Security Market Security And Protection On The Adoption And Decency Of The Data And Network
Technological evolution in computer, information can be transferred in digital way has increased rapidly. So, there are so many applications such as data processing systems, electronic mail systems, and bank system. In these applications the transferred information must pass through communications channels that can be monitored by electronic auditor.While the degree of security may be different for different application, as it should generally pass important information directly from sender to a deliberate receiver intermediate parties being able to explicate the transferred message and without any loss of information.
Furthermore, information that is saved in memory bank of computer must be secure from threats. Cryptographic security is used to transfer a message between remote locations and to send information from one end to another end every system should include at least one encoding devices at one location and one decoding device at a second location. Cryptographic security decoding and encoding technology are available to protect the authentication and privacy for communication devices.
Technological development and the need for remote access security and wireless communication is increased due to this cryptography security application that provides security and protection on the adoption and decency of the data and network.
Request Brochure: https://www.transparencymarketresearch.com/sample/sample.php?flag=B&rep_id=35813
The ongoing advancements is increasing continuously in the internet, technology and the development of new computers to support remote computation has led to increase in the requirement of network security for the secure data transmission.
Some of the main challenging factors are low customer awareness about cryptography security, and lack of expertise and skilled manpower are obstructing the growth of the Cryptographic security market. The cryptography security market is witnessing a stable growth with rising security threats, lack of the ability to acknowledge such attacks.
The quality performance of cryptographic security is depend on the complication of the decoding and encoding devices. The problem regarding privacy of communication for a system where an auditor can listen to every transmitted message on the communication channel.
The Cryptographic security market can be segmented by hardware, services, organization size, application and geographical regions. By Hardware, the market can be segmented into blade, server, random number generator and research & development platform.
The hardware is the main equipment of the Cryptographic security to make possible effective content transfer with secure system. The Most of the vendors are updating their hardware setup to maintain a competition in the Cryptographic market. By Services, the market can be bifurcated into consulting services, support and maintenance services and integration and deployment Services.
By Organization, the cryptographic security market can be segmented as large enterprises and small & medium-sized enterprises. According to the application, the cryptographic security market segment can be bifurcated as IT & telecom, network security, government & defense, database security, consumer goods & retail, healthcare & life sciences, banking, financial services & insurance and others.
Furthermore, the Cryptographic security market can also be studied according to regional bifurcations such as North America, Europe, Asia Pacific, Middle East & Africa and South America.
Moreover, with the feeling of enchanting experience, increase in demand, growth of technology and advancement in security system is expected to positively support the growth of cryptographic security market during the forecast periods. The cryptographic security market has seen huge growth in defense and banking industry in recent years.
Many players are involved in the Cryptographic Security market with wider solution portfolio. Some of the key players in the cryptographic security market are Crypta Labs, IBM, HP, Id Quantique, Magiq Technologies, NEC Corporation, Infineon, Mitsubishi, Nucrypt, Qutools, Qasky, PQ Solutions, Qubitekk, Quintessencelabs, and Toshiba among others. Most of these providers are headquartered in North America region. Most of the companies to upgrade their research and development activities to introduce innovations and security methods in this field.
The report offers a comprehensive evaluation of the market. It does so via in-depth qualitative insights, historical data, and verifiable projections about market size. The projections featured in the report have been derived using proven research methodologies and assumptions.
By doing so, the research report serves as a repository of analysis and information for every facet of the market, including but not limited to: Regional markets, technology, types, and applications.
Book Now: https://www.transparencymarketresearch.com/cryptographic-security-market.html?secure=NTIxNS41&type=PB
About TMR
Transparency Market Research (TMR) is a global market intelligence company providing business information reports and services. The company’s exclusive blend of quantitative forecasting and trend analysis provides forward-looking insight for thousands of decision makers. TMR’s experienced team of analysts, researchers, and consultants use proprietary data sources and various tools and techniques to gather and analyze information.
TMR’s data repository is continuously updated and revised by a team of research experts so that it always reflects the latest trends and information. With extensive research and analysis capabilities, Transparency Market Research employs rigorous primary and secondary research techniques to develop distinctive data sets and research material for business reports.
Contact TMR
90 State Street, Suite 700
Albany, NY 12207
Tel: +1-518-618-1030
USA - Canada Toll Free: 866-552-3453
Email:sales@transparencymarketresearch.com
Website:http://www.transparencymarketresearch.com
This release was published on openPR.
Permanent link to this press release:
Copy
Please set a link in the press area of your homepage to this press release on openPR. openPR disclaims liability for any content contained in this release.
You can edit or delete your press release Cryptographic Security Market Security And Protection On The Adoption And Decency Of The Data And Network here
News-ID: 925608 • Views: …
More Releases from Transparency Market Research
Leisure Boat Market Size Forecast to USD 77.6 Billion by 2036 with Growing Deman …
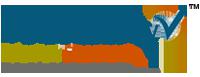
Leisure Boat Market Outlook 2036
The global leisure boat market was valued at USD 54.1 Billion in 2025 and is projected to reach USD 77.6 Billion by 2036, expanding at a steady CAGR of 3.3% from 2026 to 2036. Market growth is driven by rising recreational boating activities, increasing disposable incomes, expanding marine tourism, and growing interest in water sports and luxury lifestyles.
👉 Get your sample market research report copy today@…
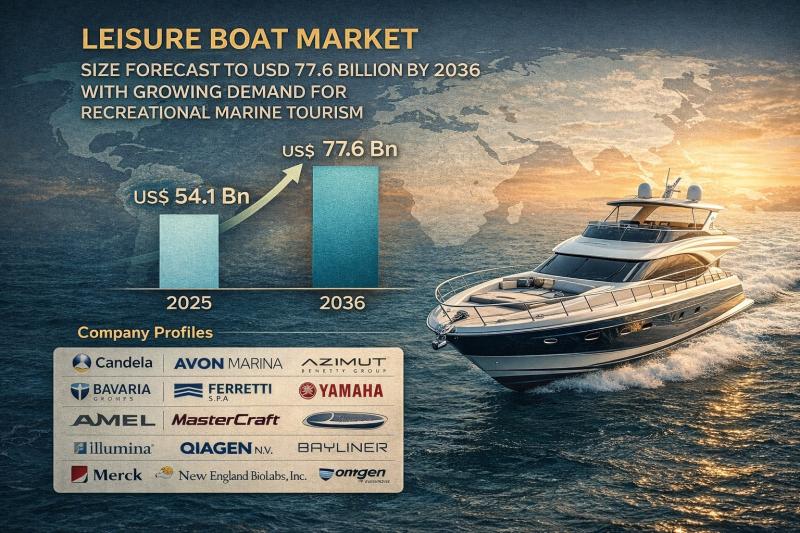
Smart/Intelligent Sensors Market to Reach USD 304 Billion by 2036, Expanding at …
The global smart/intelligent sensors market is witnessing robust expansion as connected ecosystems, automation technologies, and edge computing redefine digital infrastructure worldwide. Valued at USD 74.4 Billion in 2025, the market is projected to surge to USD 304 Billion by 2036, registering a strong CAGR of 14.3% from 2026 to 2036.
Smart or intelligent sensors go beyond conventional sensing capabilities by integrating embedded processing, data analytics, wireless connectivity, and decision-making intelligence directly…
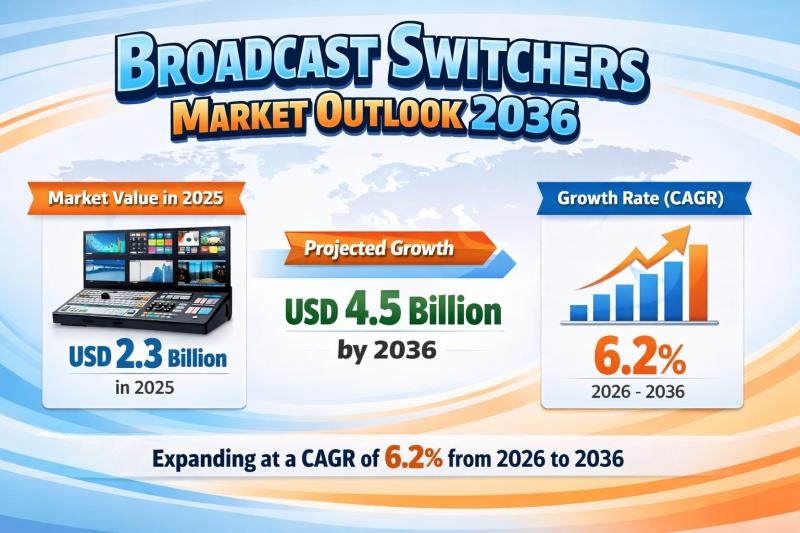
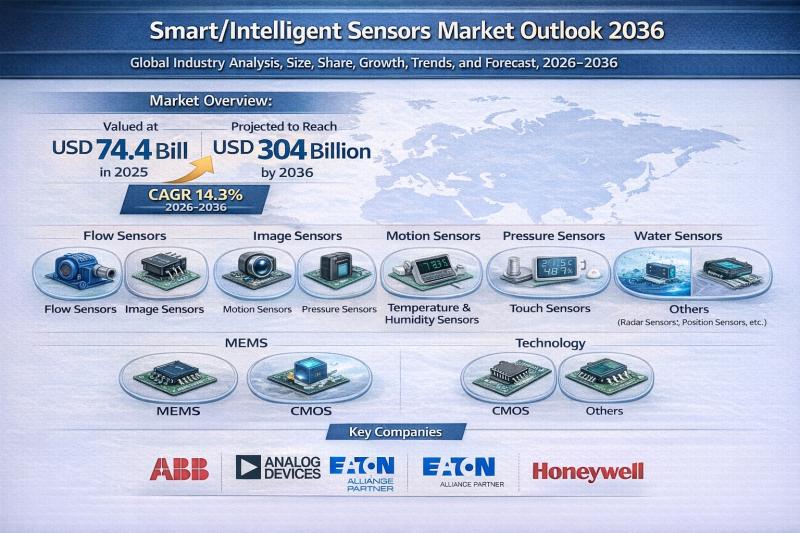
Broadcast Switchers Market to be Worth USD 4.5 Bn by 2036 - By Production, Routi …
The global Broadcast Switchers Market is poised for sustained expansion over the next decade, driven by technological innovation and rising global demand for high-quality live content production. Valued at USD 2.3 Billion in 2025, the market is projected to grow to USD 4.5 Billion by 2036, expanding at a compound annual growth rate (CAGR) of 6.2% from 2026 to 2036.
Review critical insights and findings from our Report in this sample…
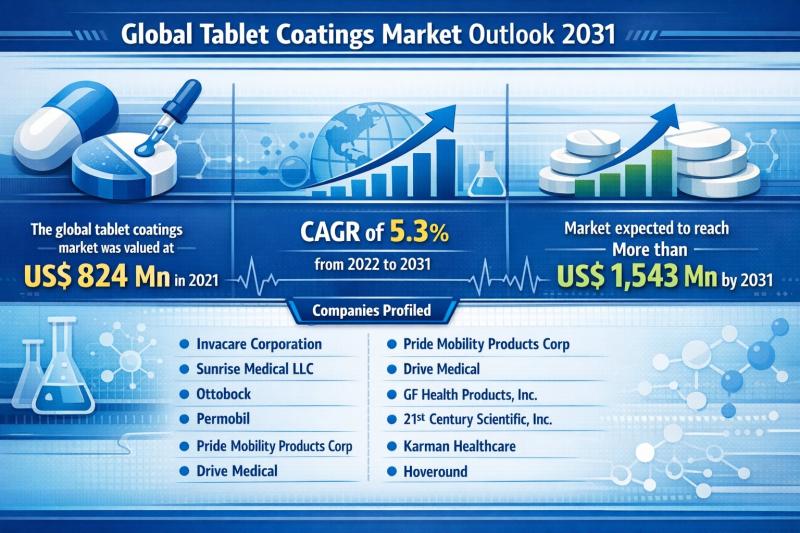
Global Tablet Coatings Market Outlook 2031: Projected to Surpass USD 1,543 Milli …
The global tablet coatings market was valued at US$ 824 Mn in 2021 and is projected to expand at a steady CAGR of 5.3% from 2022 to 2031, reaching more than US$ 1,543 Mn by 2031. This consistent growth trajectory reflects the rising consumption of coated pharmaceutical and nutraceutical tablets across developed and emerging markets.
Between 2017 and 2020, the market experienced moderate expansion driven by generics penetration and increasing oral…
More Releases for Cryptographic
The Financial Sector's Cryptographic Solutions Drive the Global Fintech Blockcha …
Inkwood Research anticipates that the Global Fintech Blockchain Market will accelerate with a 40.66% CAGR and generate $xx million during the forecast period, 2023-2032.
Refer to the Report Summary Here: https://inkwoodresearch.com/reports/fintech-blockchain-market/?utm_source=PaidPRNew&utm_medium=OpenPR&utm_campaign=InkwoodPR
This insightful market research report by Inkwood Research focuses on market trends, leading players, supply chain trends, technological innovations, key developments, and future strategies. The report covers all the aspects of this comprehensive market by assessing major geographies and is a…
Cryptographic Security Market is Booming Worldwide | Crypta Labs, IBM, HP
Advance Market Analytics published a new research publication on "Cryptographic Security Market Insights, to 2028" with 232 pages and enriched with self-explained Tables and charts in presentable format. In the Study you will find new evolving Trends, Drivers, Restraints, Opportunities generated by targeting market associated stakeholders. The growth of the Cryptographic Security market was mainly driven by the increasing R&D spending across the world.
Some of the key players profiled in…
Call for Papers for the Second International Cryptographic Module Conference
Mark Your Calendar: ICMC 2014, November 19-21, Hilton Washington D.C., Rockville, MD
ICMC brings together experts from around the world to confer on the topic of cryptographic modules, with emphasis on their secure design, implementation, assurance, and use, referencing both new and established standards such as FIPS 140-2 and ISO/IEC 19790.
We are focused on attracting participants from the engineering and research community, test laboratories, government organizations, the procurers, deployers and administrators…
Call for papers: International Cryptographic Module Conference 2013
This first ICMC aims to bring together experts from around the world to confer on the topic of cryptographic modules, with emphasis on their secure design, implementation, assurance, and use, referencing both new and established standards such as FIPS 140-2 and ISO/IEC 19790.
We are focused on attracting participants from the engineering and research community, test laboratories, government organizations, the procurers, deployers and administrators of cryptographic modules and academia. Our program…
atsec information security completes the CAVP cryptographic algorithm testing fo …
Beijing, China – atsec information security is pleased to announce that the cryptographic algorithms implemented in the Watchdata-FIPS-TimeCOS Hardware Cryptographic Library were tested by atsec information security and validated under the CAVP (Cryptographic Algorithm Validation Program) by NIST (National Institute of Standards and Technology).
The implemented algorithms of Watchdata-FIPS-TimeCOS Hardware Cryptographic Library and their validation numbers are as follows:
TDES, CMAC (No.1057)
AES (No.1616)
SHA (No.1425)
RSA (No.794)
DRBG (No.85)
More product and manufacturer information can be…
atsec tests Pierson MIIKOO cryptographic algorithms
Beijing China – Recently, atsec information security tested the cryptographic algorithms implemented by Pierson Capital Technology in its MIIKOO product. Testing included two FIPS Approved cryptographic algorithms validated under the Cryptographic Algorithm Validation Program (CAVP) by the U.S. National Institute of Standards and Technology (NIST), and also another two non-FIPS Approved cryptographic algorithms — HOTP and CRC-32. atsec performed source code review and independent testing on the two algorithms.
The NIST…