Press release
Positive Technologies Report Examines the Evolution and Current Threat of Rootkits
Difficult and Costly to Create, These Malicious Programs That Hide the Presence of Malware Target Governments and Research Institutes, and Are Here to StayNovember 3, 2021 – In a new report, Positive Technologies analyzes this past decade's most infamous families of rootkits—programs that hide the presence of malicious software or traces of intrusion in victim systems. The study finds that the majority of rootkits are used by APT groups or financially motivated criminals whose payouts exceed the costs, the most commonly targeted are government and research institutes, and 77% of rootkits are used by cybercriminals for espionage purposes.
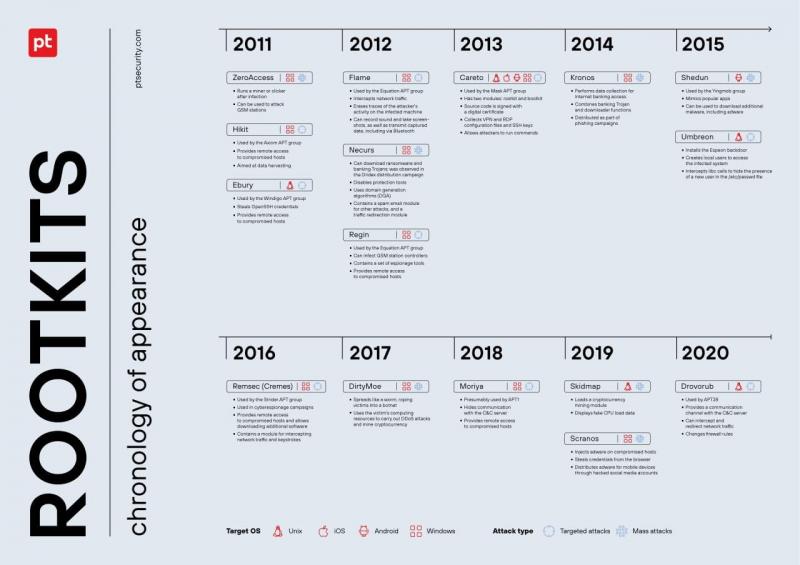
Rootkits are not the most common type of malware. Rootkit detections tend to be associated with high-profile attacks having high-impact consequences—often these tools form part of multifunctional malware that intercepts network traffic, spies on users, steals login credentials, or hijacks resources to carry out DDoS attacks. The most famous application of a rootkit in an attack was the Stuxnet campaign, which targeted Iran's nuclear program.
Positive Technologies carried out a large-scale study of rootkits used by hacker groups over the past decade, starting in 2011. The results show that in 44% of cases, cybercriminals used rootkits to attack government agencies. Slightly less frequently (38%), rootkits were used to attack research institutes. Experts link the choice of targets to the main motive of rootkit distributors: Data harvesting. The information handled by government and research organizations is of great value to cybercriminals. According to the study, the top 5 industries most attacked by rootkits also include telecommunications (25%), manufacturing (19%), and financial institutions (19%). In addition, more than half (56%) are used by hackers to attack individuals. These are mainly targeted attacks as part of cyberespionage campaigns against high-ranking officials, diplomats, and employees of victim organizations.
“Rootkits, especially ones that operate in kernel mode , are very difficult to develop, so they are deployed either by sophisticated APT groups that have the skills to develop these tools, or by groups with the financial means to buy rootkits on the gray market,” explains Yana Yurakova, a security analyst at Positive Technologies. “Attackers of this caliber are mainly focused on cyberespionage and data harvesting. They can be either financially motivated criminals looking to steal large sums of money, or groups mining information and damaging the victim's infrastructure on behalf of a paymaster.”
In 77% of cases, the rootkit families under investigation were used to harvest data, around a third (31%) were motivated by financial gain, and just 15% of attacks sought to exploit the victim company's infrastructure to carry out subsequent attacks.
The study also finds that dark web forums are dominated by ads selling user-level rootkits , which are commonly used in mass attacks. According to the report, the cost of an off-the-shelf rootkit ranges from $45,000 to $100,000, depending on the operating mode, target Operating System, terms of use (for example, time limits on how long the malware can be rented), and additional features—remote access and concealment of files, processes, and network activity are the most commonly requested. In some cases, developers offer to customize the rootkit for the buyer's needs and provide support. 67% of ads stated that the rootkit should be "tailored" for Windows. This correlates with the results of the study: Rootkits crafted for Windows systems in the sample group analyzed by Positive Technologies accounted for the lion's share (69%).
“Despite the difficulties of developing such programs, every year we see the emergence of new versions of rootkits with a different operating mechanism to that of known malware,” said Alexey Vishnyakov, Head of Malware Detection at the Positive Technologies Expert Security Center (PT ESC), which regularly tracks hacker group activity and the emergence of new information security threats. “This indicates that cybercriminals are still developing tools to disguise malicious activity and coming up with new techniques for bypassing security—a new version of Windows appears, and malware developers immediately create rootkits for it. We expect rootkits to carry on being used by well-organized APT groups, which means it's no longer just about compromising data and extracting financial gain, but about concealing complex targeted attacks that can entail unacceptable consequences for organizations—from disabling critical infrastructure, such as nuclear power stations, thermal power plants, and power grids, to anthropogenic accidents and disasters at industrial enterprises, and political espionage.”
Positive Technologies researchers believe rootkits will continue to be developed and used by cybercriminals, and in fact, PT ESC specialists have identified the emergence of new versions of rootkits, indicating that attackers continue to invent new techniques to bypass protection. A criminal’s advantages for using rootkits – executing code in privileged mode, being able to hide from security tools, and remaining online for long periods of time – are too important for attackers to reject these tools. The main danger of rootkits will continue to be the concealment of complex, targeted attacks until the point of an actual assault or set of events causing damage for the target organization.
To protect your company from rootkit-based attacks, Positive Technologies recommends using endpoint malware detection tools and solutions, such as PT Sandbox, which can identify malware during both installation and operation. A rootkit scanner, system integrity checks, and network traffic analysis for anomalies will also help detect rootkits.
8 Preobrazhenskaya Square, Moscow, 107061
CONTACT:
Paula Dunne
CONTOS DUNNE COMMUNICATIONS
+1-408-893-8750 (m)
+1-408-776-1400 (o)
paula@contosdunne.com
About Positive Technologies
Positive Technologies is a leading global provider of enterprise security solutions for vulnerability and compliance management, incident and threat analysis, and application protection. Commitment to clients and research has earned Positive Technologies a reputation as one of the foremost authorities on Industrial Control System, Banking, Telecom, Web Application, and ERP security, supported by recognition from the analyst community.
ptsecurity.com, facebook.com/PositiveTechnologies, facebook.com/PHDays.
This release was published on openPR.
Permanent link to this press release:
Copy
Please set a link in the press area of your homepage to this press release on openPR. openPR disclaims liability for any content contained in this release.
You can edit or delete your press release Positive Technologies Report Examines the Evolution and Current Threat of Rootkits here
News-ID: 2452308 • Views: …
More Releases from Positive Technologies

New Report from Positive Technologies Finds Ransomware Attacks Have Reached ‘S …
September 22, 2021 – Ransomware attacks have reached ‘stratospheric’ levels, now accounting for 69% of all attacks involving malware. That is among the most disturbing finding in “Cybersecurity Threatscape: Q2 2021,” the latest report from security specialist Positive Technologies. The research also reveals that the volume of attacks on governmental institutions in particular soared from 12% in Q1 2021 to 20% in Q2. And the company’s Expert Security Center (PT…
More Releases for Rootkit
Global Rootkit Scanner Market Set to Reach USD 1.2 billion by Key Players:Malwar …
New Jersey, US State: "The global Rootkit Scanner market in the Information Technology and Telecom category is projected to reach USD 1.2 billion by 2031, growing at a CAGR of 12.5% from 2025 to 2031. With rising industrial adoption and continuous inOctation in Information Technology and Telecom applications, the market is estimated to hit USD 450 million in 2024, highlighting strong growth potential throughout the forecast period."
Rootkit Scanner Market Size…
Rootkit Scanner Market Size by Type, Application, and Regional Outlook
USA, New Jersey- According to Market Research Intellect, the global Rootkit Scanner market in the Internet, Communication and Technology category is projected to witness significant growth from 2025 to 2032. Market dynamics, technological advancements, and evolving consumer demand are expected to drive expansion during this period.
The Rootkit Scanner market is expanding rapidly as cyber threats continue to evolve, driving the need for advanced security solutions. Rootkits, which are malicious software…
Rootkit Scanner Market Size and Forecast
𝐔𝐒𝐀, 𝐍𝐞𝐰 𝐉𝐞𝐫𝐬𝐞𝐲- The global Rootkit Scanner Market is expected to record a CAGR of XX.X% from 2024 to 2031 In 2024, the market size is projected to reach a valuation of USD XX.X Billion. By 2031 the valuation is anticipated to reach USD XX.X Billion.
Rootkit Scanner Market Size And Scope
The rootkit scanner market is expanding rapidly, driven by the increasing need for cybersecurity solutions to protect systems from malicious…
Detailed Analysis of Rootkit Scanner Market Business Growth, Development Factors …
The Rootkit Scanner Market research study is a professional report with premium insights into the size of the business, current patterns, drivers, risks, potential outcomes, and major segments. The Industry Report forecasts the future growth of the market based on precise assumptions. Furthermore, based on input from industry experts, the report provides actionable insights into the Rootkit Scanner market's future growth to assist readers in developing effective strategies. The research…
Rootkit Scanner Market Outlook 2021- Explains COVID-19 Impact, Share and Future …
Rootkit Scanner market study offers an all-inclusive analysis of the major strategies, corporate models, and market shares of the most noticeable players in this market. The company profile section of the report examines its operational structure, significant products and services offering, geographic footprints and subsidiaries, key management executives, and their biographies, along with primary and closest peer competitors.
Download FREE Sample Report @ https://www.reportsnreports.com/contacts/requestsample.aspx?name=4982380
Top Key Players are covered in this…
Rootkit Scanner Market Precise Outlook – McAfee, Symantec, Kaspersky Lab, Avas …
MarketInsightsReports, a leading global market research firm, is pleased to announce its new report on Rootkit Scanner market, forecast for 2021-2027, covering all aspects of the market and providing up-to-date data on current trends.
The Rootkit Scanner Market report provides the overall structure and business outlook of the global and regional industries. The study also involves the important Achievements of the market, Research & Development, new product launch, product responses, and…