Press release
Security and Vulnerability Management Market Competitive Outlook | Dell, IBM Corporation, McAfee, LLC, Micro Focus, Tripwire, Inc., Symantec Corporation, Skybox Security
Global security and vulnerability management market is growing at a healthy CAGR of 10.28% during the forecast period of 2019 to 2026. The upcoming market report contains data for historic year 2017, the base year of calculation is 2018 and the forecast period is 2019 to 2026.If you are involved in the Security and Vulnerability Management industry or intend to be, then this study will provide you comprehensive outlook. It's vital you keep your market knowledge up to date†segmented By Global Security and Vulnerability Management Market By Type (Solutions, Services), End User (SMBs, Enterprise), Verticals (BFSI, Government & Defence, Energy & Utilities, Healthcare, IT & Telecom, Retail, Others), Geography (North America, South America, Europe, Asia-Pacific, Middle East and Africa). - Industry Trends and Forecast to 2026
Click Here To Get Security and Vulnerability Management Market Research Sample PDF Copy @ https://www.databridgemarketresearch.com/request-a-sample/?dbmr=global-security-and-vulnerability-management-market&AM
Few of the major competitors currently working in global security and vulnerability management market are Dell, IBM Corporation, McAfee, LLC, Micro Focus, Tripwire, Inc., Symantec Corporation, Skybox Security, Inc., AlienVault, Qualys, Inc., Tenable, Inc., HP Development Company, L.P., Rapid7, FUJITSU and NetSPI LLC among others.
†This market report provides best solutions for strategy development and implementation depending on client's needs to extract tangible results. A team of experienced and consummate market research professionals persistently track key industries to spot key developments, unmet needs and possible growth opportunities. A numerous markets, marketing strategies, trends, future products and rising opportunities have been considered while studying market for preparing this Security and Vulnerability Management report. This market research report serves the clients by providing data and information on their business scenario with which they can stay ahead of the competition in today's rapidly changing business environment.
What are the major market growth drivers?
Increasing cyber-crimes and cyber threats will propel the market growth
Growing need for enterprise security is driving the growth of the market
Increasing demand for big data and cloud computing is also boosting the market growth
Government regulations for vulnerability may fuel the market in the forecast period
Competitive Landscape and Security and Vulnerability Management Market Share Analysis
Security and Vulnerability Management market competitive landscape provides details by competitor. Details included are company overview, company financials, revenue generated, market potential, investment in research and development, new market initiatives, global presence, company strengths and weaknesses, product launch, product width and breadth, application dominance. The above data points provided are only related to the companies' focus related to Security and Vulnerability Management market.
Regional and Country-level Analysis
To comprehend Global Security and Vulnerability Management market dynamics in the world mainly, the worldwide Security and Vulnerability Management market is analyzed across major global regions. DBMR also provides customized specific regional and country-level reports for the following areas.
North America: United States, Canada, and Mexico.
South & Central America: Argentina, Chile, and Brazil.
Middle East & Africa: Saudi Arabia, UAE, Turkey, Egypt and South Africa.
Europe: UK, France, Italy, Germany, Spain, NORDIC {Sweden, Norway, Finland, Denmark etc}, BENELUX {Belgium, The Netherlands, Luxembourg}, and Russia.
Asia-Pacific: India, China, Japan, South Korea, Indonesia, Singapore, and Australia.
Global Security and Vulnerability Management Market Methodology
Data Bridge Market Research†presents, all the information, statistics and data included in this Security and Vulnerability Management report is gathered from the truthful sources such as websites, newspapers, journals, white papers, mergers, and annual reports of the companies. To succeed in this competitive market place, market research report plays a very important role by offering important and consequential market insights for your business.
This involves data mining, analysis of the impact of data variables on the market, and primary (industry expert) validation. Apart from this, other data models include Vendor Positioning Grid, Market Time Line Analysis, Market Overview and Guide, Company Positioning Grid, Company Market Share Analysis, Standards of Measurement, Top to Bottom Analysis and Vendor Share Analysis. Triangulation is one method used while reviewing, synthesizing and interpreting field data. Data triangulation has been advocated as a methodological technique not only to enhance the validity of the research findings but also to achieve 'completeness' and 'confirmation' of data using multiple methods
Market Dynamics:
Set of qualitative information that includes PESTEL Analysis, PORTER Five Forces Model, Value Chain Analysis and Macro Economic factors, Regulatory Framework along with Industry Background and Overview
What Porter's Five Forces of Competitive Analysis Provides?
Supplier power:- An assessment of how easy it is for suppliers to drive up prices. This is driven by the: number of suppliers of each essential input; uniqueness of their product or service; relative size and strength of the supplier; and cost of switching from one supplier to another.
Buyer power:- An assessment of how easy it is for buyers to drive prices down. This is driven by the: number of buyers in the market; importance of each individual buyer to the organisation; and cost to the buyer of switching from one supplier to another. If a business has just a few powerful buyers, they are often able to dictate terms.
Competitive rivalry:- The main driver is the number and capability of competitors in the market. Many competitors, offering undifferentiated products and services, will reduce market attractiveness.
Threat of substitution:- †Where close substitute products exist in a market, it increases the likelihood of customers switching to alternatives in response to price increases. This reduces both the power of suppliers and the attractiveness of the market.
Threat of new entry:- Profitable markets attract new entrants, which erodes profitability. Unless incumbents have strong and durable barriers to entry, for example, patents, economies of scale, capital requirements or government policies, then profitability will decline to a competitive rate.
Five forces analysis helps organizations to understand the factors affecting profitability in a specific industry, and can help to inform decisions relating to: whether to enter a specific industry; whether to increase capacity in a specific industry; and developing competitive strategies.
Key Developments in the Market:
In January 2019, NetSPI LLC, has announced the launch of NetSPI Resolve, which is a vulnerability management solution that gives an end-to-end solution. It helps the customers to fix vulnerabilities faster for security of their data. This development helps the company to enhance their product portfolio
In January 2017, Tata Communications has launched the global availability of their vulnerability management service (VMS). This VMS is a part of managed security services suite and it is built on QualysGuard vulnerability management and compliance solutions. This development helps the company to cater more customers globally
Key Insights that Study is going to provide:
The 360-degree Security and Vulnerability Management overview based on a global and regional level
Market Share & Sales Revenue by Key Players & Emerging Regional Players
Competitors - In this section, various Security and Vulnerability Management industry leading players are studied with respect to their company profile, product portfolio, capacity, price, cost, and revenue.
A separate chapter on Market Entropy to gain insights on Leaders aggressiveness towards market [Merger & Acquisition / Recent Investment and Key Developments]
Patent Analysis** No of patents / Trademark filed in recent years.
A complete and useful guide for new market aspirants
Forecast information will drive strategic, innovative and profitable business plans and SWOT analysis of players will pave the way for growth opportunities, risk analysis, investment feasibility and recommendations
Supply and Consumption - In continuation of sales, this section studies supply and consumption for the Security and Vulnerability Management Market. This part also sheds light on the gap between supply and consumption. Import and export figures are also given in this part
Production Analysis - Production of the Security and Vulnerability Management is analyzed with respect to different regions, types and applications. Here, price analysis of various Security and Vulnerability Management Market key players is also covered.
Sales and Revenue Analysis - Both, sales and revenue are studied for the different regions of the Security and Vulnerability Management Market. Another major aspect, price, which plays an important part in the revenue generation, is also assessed in this section for the various regions.
Other analyses - Apart from the information, trade and distribution analysis for the Security and Vulnerability Management Market
Competitive Landscape: Company profile for listed players with SWOT Analysis, Business Overview, Product/Services Specification, Business Headquarter, Downstream Buyers and Upstream Suppliers.
May vary depending upon availability and feasibility of data with respect to Industry targeted
TABLE OF CONTENTS
Part 01: Executive Summary
Part 02: Scope Of The Report
Part 03: Research Methodology
Part 04: Market Landscape
Part 05: Pipeline Analysis
Part 06: Market Sizing
Part 07: Five Forces Analysis
Part 08: Market Segmentation
Part 09: Customer Landscape
Part 10: Regional Landscape
Part 11: Decision Framework
Part 12: Drivers And Challenges
Part 13: Market Trends
Part 14: Vendor Landscape
Part 15: Vendor Analysis
Part 16: Appendix
Thanks for reading this article; you can also get individual chapter wise section or region wise report version like North America, Europe, MEA or Asia Pacific.
Browse TOC with selected illustrations and example pages of Security and Vulnerability Management market @ https://www.databridgemarketresearch.com/toc/?dbmr=global-security-and-vulnerability-management-market&AM
Contact:
Data Bridge Market Research
US: +1 888 387 2818
UK: +44 208 089 1725
Hong Kong: +852 8192 7475
Email:†Corporatesales@databridgemarketresearch.com
About Data Bridge Market Research:
An absolute way to forecast what future holds is to comprehend the trend today!
Data Bridge set forth itself as an unconventional and neoteric Market research and consulting firm with unparalleled level of resilience and integrated approaches. We are determined to unearth the best market opportunities and foster efficient information for your business to thrive in the market. Data Bridge endeavors to provide appropriate solutions to the complex business challenges and initiates an effortless decision-making process.
Data Bridge adepts in creating satisfied clients who reckon upon our services and rely on our hard work with certitude. We are content with our glorious 99.9 % client satisfying rate.
This release was published on openPR.
Permanent link to this press release:
Copy
Please set a link in the press area of your homepage to this press release on openPR. openPR disclaims liability for any content contained in this release.
You can edit or delete your press release Security and Vulnerability Management Market Competitive Outlook | Dell, IBM Corporation, McAfee, LLC, Micro Focus, Tripwire, Inc., Symantec Corporation, Skybox Security here
News-ID: 1947883 • Views: ‚Ķ
More Releases from Data Bridge Market Research

Scented Candle Market Shows Strong Growth Driven by Wellness and Home DeŐĀcor Tr ‚Ķ
The global scented candle market is on track for significant expansion, increasing from an estimated USD 3.60 billion in 2024 to USD 6.00 billion by 2032, registering a strong CAGR of 6.60%. Rising consumer interest in home ambiance, wellness, and premium lifestyle products continues to drive market demand.
Get More Detail: https://www.databridgemarketresearch.com/reports/global-scented-candle-market
Market Growth Drivers
The scented candle market has evolved beyond being just a decorative item. Key growth factors include:
Home Fragrance &…
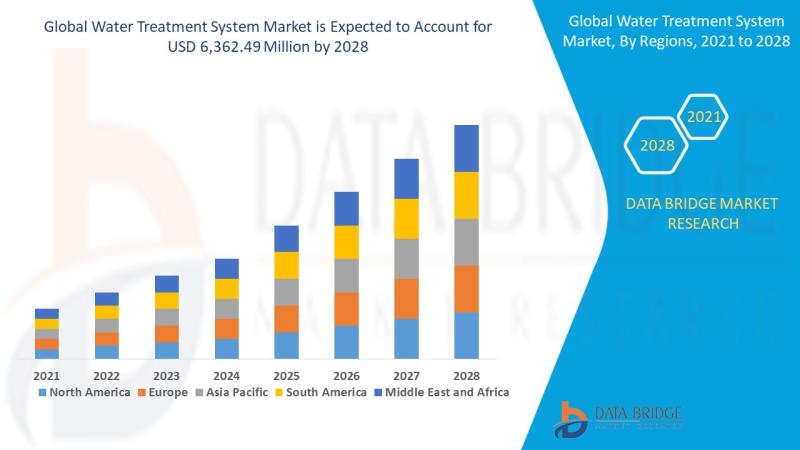
Water Treatment System Market: Sustaining the Future of Clean Water
Introduction
Understanding Water Treatment Systems
Water treatment systems are designed to purify and disinfect water for various uses-drinking, industrial processes, irrigation, and wastewater reuse. These systems eliminate contaminants such as bacteria, viruses, heavy metals, chemicals, and particulates, making water safe and sustainable for consumption and use.
Importance in Global Sustainability
Clean water is essential to life and industrial progress. With growing water demand and pollution, water treatment systems are now critical infrastructure across the…

Veterinary X-Ray Market Size, Analysis, Scope, Demand, Opportunities, Statistics
According to Data Bridge Market Research The global Veterinary X-Ray market size was valued at USD 915.19 million in 2024 and is projected to reach USD 1576.00 million by 2032, with a CAGR of 7.03 % during the forecast period of 2025 to 2032.
With increasing globalization and digital disruption, the Equine X-Ray Solutions Market is expanding across multiple industries, . Market research data indicates that businesses in the Companion Animal…

Veterinary X-Ray Market Size, Analysis, Scope, Demand, Opportunities, Statistics
According to Data Bridge Market Research The global Veterinary X-Ray market size was valued at USD 915.19 million in 2024 and is projected to reach USD 1576.00 million by 2032, with a CAGR of 7.03 % during the forecast period of 2025 to 2032.
With increasing globalization and digital disruption, the Equine X-Ray Solutions Market is expanding across multiple industries, . Market research data indicates that businesses in the Companion Animal…
More Releases for Security
Aerospace Cyber Security Market : Network security, Wireless security, Cloud sec …
According to a new report published by Allied Market Research, titled, "Aerospace Cyber Security Market," The aerospace cyber security market was valued at $39.7 billion in 2021, and is estimated to reach $92.0 billion by 2031, growing at a CAGR of 9.0% from 2022 to 2031.
ūĚźÉūĚź®ūĚźįūĚźßūĚź•ūĚź®ūĚźöūĚźĚ ūĚźĎūĚźěūĚź©ūĚź®ūĚźęūĚź≠ ūĚźíūĚźöūĚź¶ūĚź©ūĚź•ūĚźě ūĚźŹūĚźÉūĚźÖ : https://www.alliedmarketresearch.com/request-sample/9433
Aerospace cybersecurity is a security driven technology which is dedicated towards the safety & security of aircrafts, spacecrafts and drones…
Healthcare Cyber Security Market by Type (Service and Solution), Security (Appli …
Healthcare Cyber Security Market: 2023
The global Healthcare Cyber Security Market size was valued at USD 4,591 Million in 2016, and is projected to reach at USD 12,467 Million by 2023, with a CAGR of 15.6% from 2017 to 2023.
Covid-19 latest section covered in this report.
Get Free Sample: https://reports.valuates.com/request/sample/ALLI-Auto-1J168/Healthcare_Cyber_Security
Cyber security solutions and services enable healthcare organizations to protect their business-critical infrastructure and patient data, and meet regulatory compliance.
Increase…
Aerospace Cyber Security Market Analysis and Forecasts by Security Type (Network …
The aviation industry is one of the sophisticated industries across the globe and the industry is integrated with advanced technological solutions. This has created a major concern towards securing the enormous quantity of data being generated every day. With the advancements in the different technological fields, the cyber attackers are also finding newer process to gain desired insights. In the current market scenario, aerospace industry is also witnessing substantial upswing…
Security Assessment Market Report 2018: Segmentation by Security Type (Endpoint …
Global Security Assessment market research report provides company profile for Kaspersky (Russia), IBM (US), FireEye (US), Optiv Security (US), Qualys (US), Trustwave (US), Veracode (US), Check Point (Israel), Absolute Software (Canada), Rapid7 (US), CynergisTek (US) and Others.
This market study includes data about consumer perspective, comprehensive analysis, statistics, market share, company performances (Stocks), historical analysis 2012 to 2017, market forecast 2018 to 2025 in terms of volume, revenue, YOY growth…
The Mobile Security (mSecurity) Bible: 2014 - 2020 - Device Security, Infrastruc …
Mobile networks around the globe generate more than 86 Exabytes of traffic annually. The immense volume of traffic together with the growing adoption of open source Operating System (OS) platforms such as Android has opened up new security threats. Mobile malware, SMS spam, cyber attacks and unlawful eavesdropping are an ever-increasing problem for enterprises, consumers and mobile network operators around the globe.
This has in turn led to significant investments in…
Mobile Security (MSecurity) Market Analysis To 2020 - Device Security, Infrastru …
Mobile networks around the globe generate more than 86 Exabytes of traffic annually. The immense volume of traffic together with the growing adoption of open source Operating System (OS) platforms such as Android has opened up new security threats. Mobile malware, SMS spam, cyber attacks and unlawful eavesdropping are an ever-increasing problem for enterprises, consumers and mobile network operators around the globe.
This has in turn led to significant investments in…
