Press release
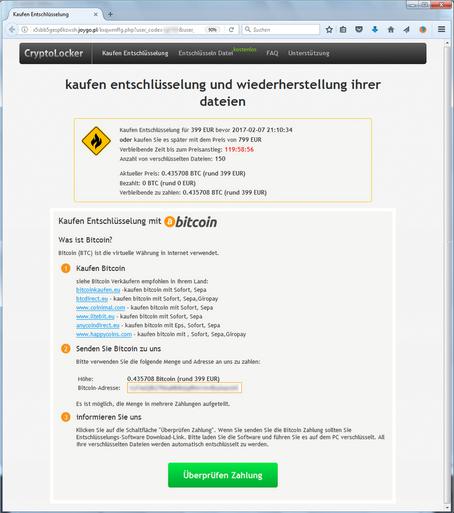
How Cryptolocker trojan uses dropbox and O2 bills to spread itself?
There are PC threats that no longer pose risk once removed. In contrast to this virus majority, even after a virus Trojan is eliminated, its effects persevere. Files affected by the CryptoLocker ransomware are not recoverable unless the victim agrees to the terms of the imposed buyout and submits Bitcoin payment to the extortionists. Currently Cryptolocker is sitting at the top of the cybercrime hierarchy together with Cerber and Locky.Operators of the Cryptolocker trojan fraud appear to be exercising their extortion skills in several ways. During the last time they tried to use fake Dropbox emails and fake O2 bills to distribute this ransomware in Europe. Though, the biggest chance to encounter Cryptolocker ransomware and other ransomware viruses is to click on a malicious email attachment. We want to point out that even safe looking Word, Excel or PDF or other documents might include a payload. Thus, you should not rush opening email attachments. First of all, attentively read the message several times, look for the grammar or spelling mistakes, check credentials, etc.
Having completed the trespass, the Cryptolocker ransomware looks for more than 500 file formats on the hard drive, network drives if any, and removable media. In the meanwhile, it ignores some of the system-level directories, including Windows, AppData, Program Files, and Temp. Then, the items matching the hard-coded range of extensions get encrypted with AES algorythm. The look of encoded files is changed drastically: the name of each one gets replaced with a lengthy array of numbers and characters, with the 5 numbers and letters string, appending them at the end.
Specific ransom instruction files are additional attributes of this virus. The ransomware creates documents on the desktop and in temp folder as long as it holds locked files like: rxojsiry.exe or nsz7022.tmpSystem.dll. These basically repeat the same info: pay Bitcoins, get the key, decrypt the data. All in all, submitting the money is the last thing to do. Before even pondering over paying, do not fail to try the techniques that can upset the cybercriminals. What is more, don’t forget to keep all installed software up-to-date and strengthen your computer’s security with anti-malware program. Lastly, you should also make data backups because no one can be 100% protected from the malware.
https://www.virus-entferner.de/2017/03/25/cryptolocker-dropbox-virus-entfernen/
Virus-Entferner Team
The project Virus-Entferner is an informational website, which provides different informations about new ransomware, malware, spyware and trojan. The company is located in Germany. It was founded in 2015 by the students and passionate computer security experts at the university of Duisburg-Essen with the aim to protect people form different web-viruses and to give them information about computer protection. All this time we have been working as the publisher and the developer of virus-entferner.de. Of course, today we are not alone behind this project. We try to support everyone who needs help and who has problems with malware, ransomware and other PC threats.
Sabine Klaske
Tulpenstrasse 10-14
47057 Duisburg
Germany
Tel: 015166031058
This release was published on openPR.
Permanent link to this press release:
Copy
Please set a link in the press area of your homepage to this press release on openPR. openPR disclaims liability for any content contained in this release.
You can edit or delete your press release How Cryptolocker trojan uses dropbox and O2 bills to spread itself? here
News-ID: 486080 • Views: …
More Releases from Virus-Entferner

Cerber 3 ransomware trojan is the most dangerous virus of september 2016
The new Cerber3 ransomware is now released. The current third Type happens to be one of the most developed and destructive file-encrypting virtual threats. It has developed its form and it is even able to speak to its victims. The hackers did not give any opportunity for trojan researchers to obtain the advantage and regularly come up with the improved versions. However, if the latest version of the Cerber3…
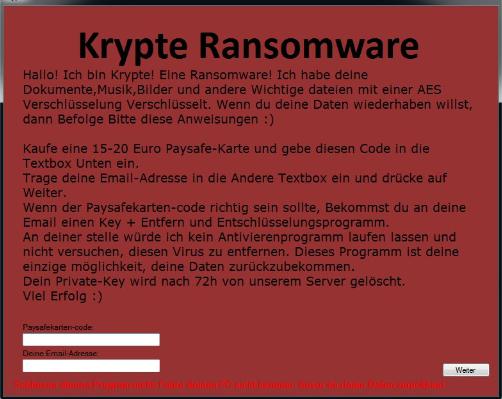
Krypte Virus .fear Ransomware targets German web-users
Krypte PC Virus falls into the category of ransomware because it is designed to encrypt files and demand money to give them free. Unfortunately, you might not be able to decrypt your crypted files using a third-party decryption, and you cannot be certain that this ransom’s developer will send you the decryption key once you have paid. Therefore, malware researches suggest that you remove this ransomware and wait for a…
More Releases for Cryptolocker
The biggest threat to your business might be talking to you now
(25 AUGUST 2016, LONDON, UNITED KINGDOM) There is another threat to your business. A real threat; one you speak to every day and one that may not know they are actually a threat to your operations. In fact, virtually all of us who work are this threat – we are employees and if we are uninformed about our roles, we can be the most dangerous person in your office.
All a…