Press release
Cerber 3 ransomware trojan is the most dangerous virus of september 2016
The new Cerber3 ransomware is now released. The current third Type happens to be one of the most developed and destructive file-encrypting virtual threats. It has developed its form and it is even able to speak to its victims. The hackers did not give any opportunity for trojan researchers to obtain the advantage and regularly come up with the improved versions. However, if the latest version of the Cerber3 occupied your computer, there is no need to worry. It is still possible to remove Cerber3 Only after it is permanently deleted from the system, you can consider data recovery possibilities. Certainly, the new update is worth interest. The ransomware is acclaimed as one of the most complex viruses.The Cerber3 ransomware emerged on the last day of august 2016, almost a month after the previous edition started compromising Windows users. The latest Cerber3 variant is a destructive fusion of this strain’s old characteristics and new features, both external and code-level ones. The properties inherited from version one and two include the Command and Control network, the specificity of cryptographic workflow, as well as the look and feel of victim interaction elements. Cerber3 trojan is still replacing an infected user’s desktop background with an image of its own containing the actual warning along with preliminary steps to start on paid decryption. Another effect that’s already familiar to researchers and victims is the scary voice coming out of the speakers that iterates the alert message.
The second version of the Cerber Ransomware was mostly notable for encrypting the files and attaching .cerber2 extension to them. Speaking of Cerber3 virus, it appends .cerber3 extension to the addicted data. Thus, within a short while, the ransomware obtained alternative title – .cerber3 extension virus. The malware now presents the instructions of file recovery not in #DECRYPT MY FILES #.txt, but in # HELP DECRYPT #.txt. Moreover, this ransomware now shifts to using ICMP packets. In short, they are error messages. You might encounter a lot of them once Cerber3 ransomware gets a hold of your operating system.
Although a lot has not been changed as compared to the earlier second variant, Cerber3 has got quite a bit of individuality that makes it unique. First of all, the tactic of renaming files is now different. The ransomware appends .cerber3 extension to every encrypted item. Filenames are impossible to recognize due to the unwelcome impact as they are substituted with 10 random symbols. 8XNZ7vX-yU.cerber3 is a sample string that demonstrates what happens to a regular document, photo, database or other file scrambled by the malicious artifact in question.
The project Virus-Entferner is an informational website, which provides different informations about new ransomware, malware, spyware and trojan. The company is located in Germany. It was founded in 2015 by the students and passionate computer security experts at the university of Duisburg-Essen with the aim to protect people form different web-viruses and to give them information about computer protection. All this time we have been working as the publisher and the developer of virus-entferner.de. Of course, today we are not alone behind this project. We try to support everyone who needs help and who has problems with malware, ransomware and other PC threats.
Sabine Klaske
Tulpenstrasse 10-14
47057 Duisburg
Tel: 015166031058
This release was published on openPR.
Permanent link to this press release:
Copy
Please set a link in the press area of your homepage to this press release on openPR. openPR disclaims liability for any content contained in this release.
You can edit or delete your press release Cerber 3 ransomware trojan is the most dangerous virus of september 2016 here
News-ID: 370749 • Views: …
More Releases from Virus-Entferner
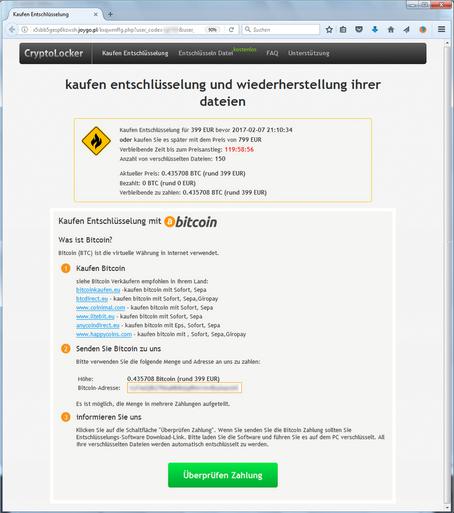
How Cryptolocker trojan uses dropbox and O2 bills to spread itself?
There are PC threats that no longer pose risk once removed. In contrast to this virus majority, even after a virus Trojan is eliminated, its effects persevere. Files affected by the CryptoLocker ransomware are not recoverable unless the victim agrees to the terms of the imposed buyout and submits Bitcoin payment to the extortionists. Currently Cryptolocker is sitting at the top of the cybercrime hierarchy together with Cerber and…
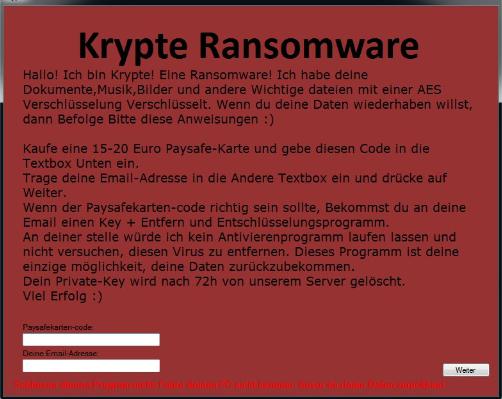
Krypte Virus .fear Ransomware targets German web-users
Krypte PC Virus falls into the category of ransomware because it is designed to encrypt files and demand money to give them free. Unfortunately, you might not be able to decrypt your crypted files using a third-party decryption, and you cannot be certain that this ransom’s developer will send you the decryption key once you have paid. Therefore, malware researches suggest that you remove this ransomware and wait for a…
More Releases for Cerber
How Cryptolocker trojan uses dropbox and O2 bills to spread itself?
There are PC threats that no longer pose risk once removed. In contrast to this virus majority, even after a virus Trojan is eliminated, its effects persevere. Files affected by the CryptoLocker ransomware are not recoverable unless the victim agrees to the terms of the imposed buyout and submits Bitcoin payment to the extortionists. Currently Cryptolocker is sitting at the top of the cybercrime hierarchy together with Cerber and…
KnowBe4 CyberAlert: Double-Barrel Ransomware and DDos Attack in-one
(Tampa Bay, FL) May 24, 2016-- KnowBe4, issued an alert today on a malicious new trend in ransomware. Instead of "just" encrypting data files on a workstation (plus any network drive it can find) and locking the machine, a new variant of the Cerber ransomware is now adding a DDoS bot that can quietly blast spoofed network traffic at various IPs.
This is the first time DDoS malware has…
