Press release
CyberCrooks Using Fake Security Program 'Cloud AV 2012' as Aggressive Money Extortion Tool
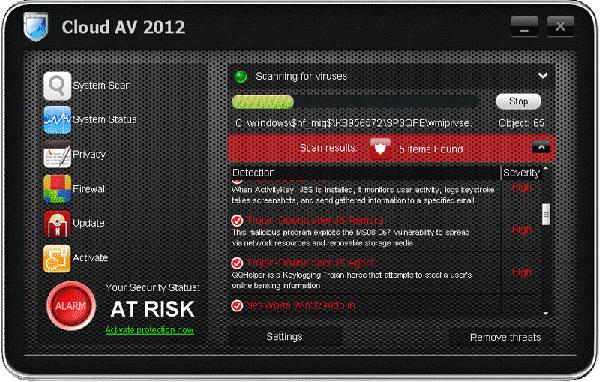
If you have noticed pop-up alerts or system scans generated by a program called Cloud AV 2012, then your PC may be infected with malware and is in need of removing the Cloud AV 2012 program.A program that goes by the name of Cloud AV 2012 has been found to be a fake anti-virus application that utilizes aggressive techniques for the purpose of extorting money from unsuspecting computer users. The technical details and removal information for Cloud AV 2012 is provided in this article.
Cloud AV 2012 is a fake security program that targets computer users using a PC usually connected to the internet. Cloud AV 2012 has been marketed and offered by cybercrooks or what some may simply call hackers. These hackers develop fake security programs usually in abundant numbers to run scams on gullible computer users.
The scam that Cloud AV 2012 conducts is one inclusive to making a computer user believe that their system is infected with different types of malware and they must use the Cloud AV 2012 program to clean those infections off. The scam ultimately commences when Cloud AV 2012 is offered as a solution to detecting and removing those so-called “exposed malware threats.” These threats are listed in misleading pop-up alerts in addition to system scans followed up with bogus parasite results.
Aside from the typical characteristics of Cloud AV 2012 previously mentioned, Cloud AV 2012 has many other symptoms that computer users must take note to. Many of these symptoms are a clear indication to a PC that is in need of being cleaned by means of a trusted and updated spyware detection program for PCs. Below is a list of common Cloud AV 2012 symptoms.
-Desktop background changed without the computer user or administrator’s action.
-Random system reboots.
-Locked programs or applications become inaccessible.
-A repetitive number of pop-up alerts imitating the Windows Security Center.
-Web browser redirects to unwanted sites.
-Blocking access to certain websites.
Removing Cloud AV 2012 has proven to be a difficult task especially if performed manually. Manual removal of Cloud AV 2012 is possible but must be performed with the utmost scrutiny and caution towards legitimate system files and those files necessary for Windows to run.
The good news about those who suffer from Cloud AV 2012 is that it has been successfully removed by utilizing updated spyware scanners such as SpyHunter. Other similar tools such as other legitimate spyware remover programs have also been successful in removing Cloud AV 2012. One of the latest released removal reports is available at: http://www.spywareremove.com/removecloudav2012.html
There are also computer technicians available over the internet that may assist computer users with removing Cloud AV 2012 but you must use extreme caution in choosing the right source. Do not use anyone. It would be conducive to use a trusted entity that has the proper credentials to help you with any computer problem you may have.
SpywareRemove.com has the answers to all your computer security needs. SpywareRemove.com is a spyware removal guide that is dedicated to providing you with the necessary tools and resources to help you fight spyware.
Enigma Software Group USA, LLC
2643 Gulf to Bay Blvd.
Suite 1560 #446
Clearwater, FL 33759
USA
This release was published on openPR.
Permanent link to this press release:
Copy
Please set a link in the press area of your homepage to this press release on openPR. openPR disclaims liability for any content contained in this release.
You can edit or delete your press release CyberCrooks Using Fake Security Program 'Cloud AV 2012' as Aggressive Money Extortion Tool here
News-ID: 202927 • Views: …
More Releases from SpywareRemove
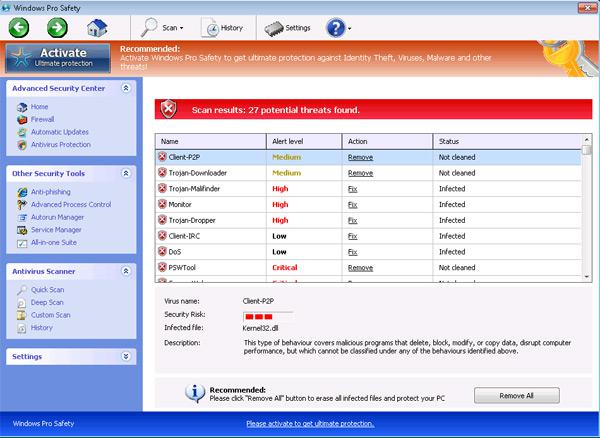
Windows Pro Safety Designed by Hackers to Mimic Legitimate PC Security Programs
Computer users around the world have a new malicious program to worry about that goes by the name of Windows Pro Safety. Windows Pro Safety is among a long list of rogue antispyware programs identified by security researchers.
The creators of programs such as Windows Pro Safety make a living out of scamming PC users. The common scams within the realm of the Windows Pro Safety program are ones that…
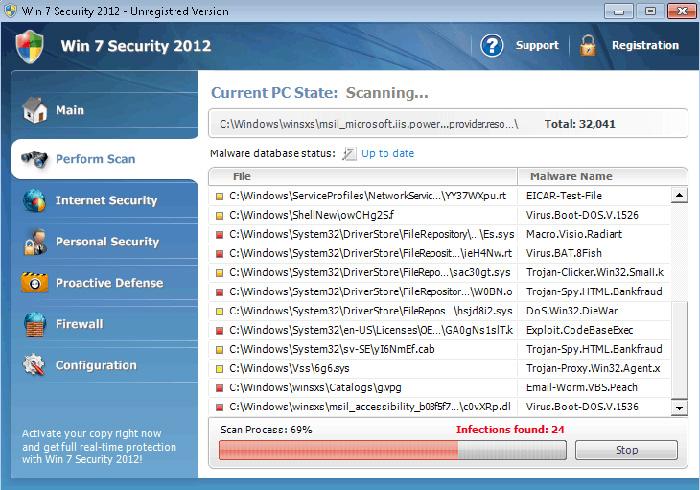
CyberThieves Market Fake Win 7 Security 2012 Security Program As A Malware Remov …
It is almost every day that new malware threats are released into the wild fields of the internet. Quite frequently security research sources over the internet release new reports warning computer users of new threats such as a fake security program called Win 7 Security 2012. One of the latest reports to grace the presence of computer users with comprehensive malware removal resources is the Win 7 Security 2012 Removal…
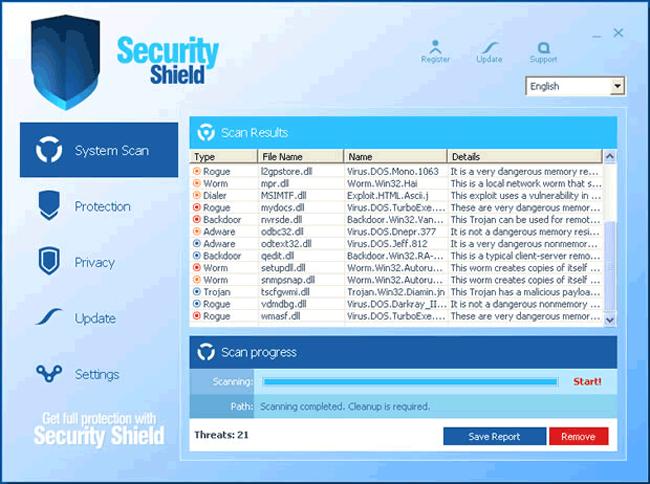
Security Shield Rogue Anti-Spyware Application Updated Removal Guide Released
The security experts at SpywareRemove.com have released an updated Security Shield Removal Guide for PC users plagued with attempting to remove Security Shield (fake security program) from their system.
The rogue anti-spyware program Security Shield has been classified by many online security research sources to be a fake security program primarily designed to thwart computer users to the point that they purchase a full version of Security Shield. The creators…
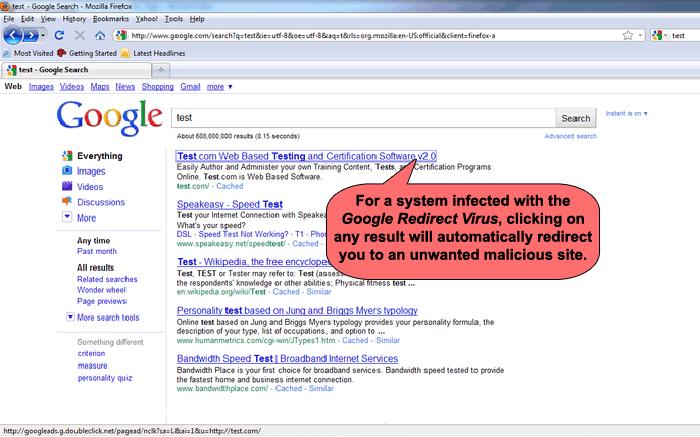
Google Redirect Virus Removal Guide Released To Help Eliminate Redirection from …
A vast number of computer users have faced a Google redirect from search results due to a Google Redirect Virus. A new Removal Guide has been released by SpywareRemove.com to stop the Google redirect from happening.
A new Google Redirect Virus Removal Guide has been released on SpywareRemove.com to assist computer users with detection and removal of a dangerous PC Trojan parasite that causes a redirect when clicking on various…
More Releases for Cloud
Customized Cloud Service Market Analysis by Company - Google Cloud Platform, Rut …
DeepResearchReports has uploaded a latest report on Customized Cloud Service Industry from its research database. Customized Cloud Service Market is segmented by Regions/Countries. All the key market aspects that influence the Customized Cloud Service Market currently and will have an impact on it have been assessed and propounded in the Customized Cloud Service Market research status and development trends reviewed in the new report.
The new tactics of Customized…
Public Cloud Market (Cloud Billing, Cloud Access Security, Cloud Communication P …
Overview
The report on the global Public Cloud market is a product of extensive research conducted by a team of industry professionals. The report discusses briefly various products or services in the market and their applications. The report provides information on the latest technologies that are used in production, manufacturing, etc in order to improve efficiency and effectiveness. The report segments the market into various categories, in order to simplify the…
Cloud Service Consultants, Cloud Consulting Service, Enterprise Cloud Management …
Overview
Ken Research is dedicated towards unraveling multipart encounters within each stage of Data Center Lifespan such as Volume Planning, Scalability Issues, Uptime, Performance Conservation and Cost. Whether you are considering improving, forming, buying, leasing or revolutionizing your prevalent data center, Ken Research can maintenance you on every aspect by smoothing you partner with Vendors who have enormous understanding in the comparable Service Offering.
However, the data centers are an influential component…
Cloud Computing for Business Operations Market 2019 By Amazon Web Services, Micr …
Cloud computing is a internet-based computing where central remote servers maintain all the data and applications. Cloud computing allow business operators to rent physical infrastructure from a third party provider(cloud service provider).
Cloud Computing for Business Operations Market reports also offer important insights which help the industry experts, product managers, CEOs, and business executives to draft their policies on various parameters including expansion, acquisition, and new product launch as well as…
Global Cloud Computing for Business Operations Market, Top key players are Amazo …
Global Cloud Computing for Business Operations Market Size, Status and Forecast 2019-2025
Cloud computing is a internet-based computing where central remote servers maintain all the data and applications. Cloud computing allow business operators to rent physical infrastructure from a third party provider (cloud service provider).
In 2018, the global Cloud Computing for Business Operations market size was xx million US$ and it is expected to reach xx million US$ by the…
Top 10 Cloud Technology Market (Hybrid Cloud, Cloud Storage, Cloud Migration, Cl …
“Top 10 Cloud Technology Market (Hybrid Cloud, Cloud Storage, Cloud Migration, Cloud Orchestration, Integration Platform As-A-Service, Disaster Recovery As-A-Service, Multi Cloud Management, Video-As-A Service, Cloud Analytics, and Wi-Fi-As-A-Service)”, Purchase This Report by calling ResearchnReports.com at +1-888-631-6977.
“Rising demand for business agility and the need for lower CAPEX and OPEX driving the growth of the cloud migration services market”
The migration to cloud enables the organizations and businesses to move their computing assets…